
Sometimes pre-installed RAM in Mac is not sufficient if your usage is more than the configuration can take. This, in turn, affects Mac’s performance...

So, you have made that great decision of jumping from Windows 10 to Windows 11. If you are already in the process, do check out the things you should ...

Every new OS has some system requirements to run the OS smoothly. Similarly, Windows 11 has some minimum system requirements to run the new OS but it ...

Among all the video-conference services such as Microsoft Teams, Zoom, and Google Meet, they had many similarities but FaceTime had to restrict its fe...

Often, we delete a file, not by shift+delete operation but, with the simple delete function, with a hope that in the near or not so near future, if we...

Your 256 GB worth of SSD soon starts to fill up real fast and one day it is filled to the brim. Even if that’s not the case, you might still see tha...

In this day and age, video calls have become a necessity. Whether it be numerous office meetings or online classes, video calls have become an importa...

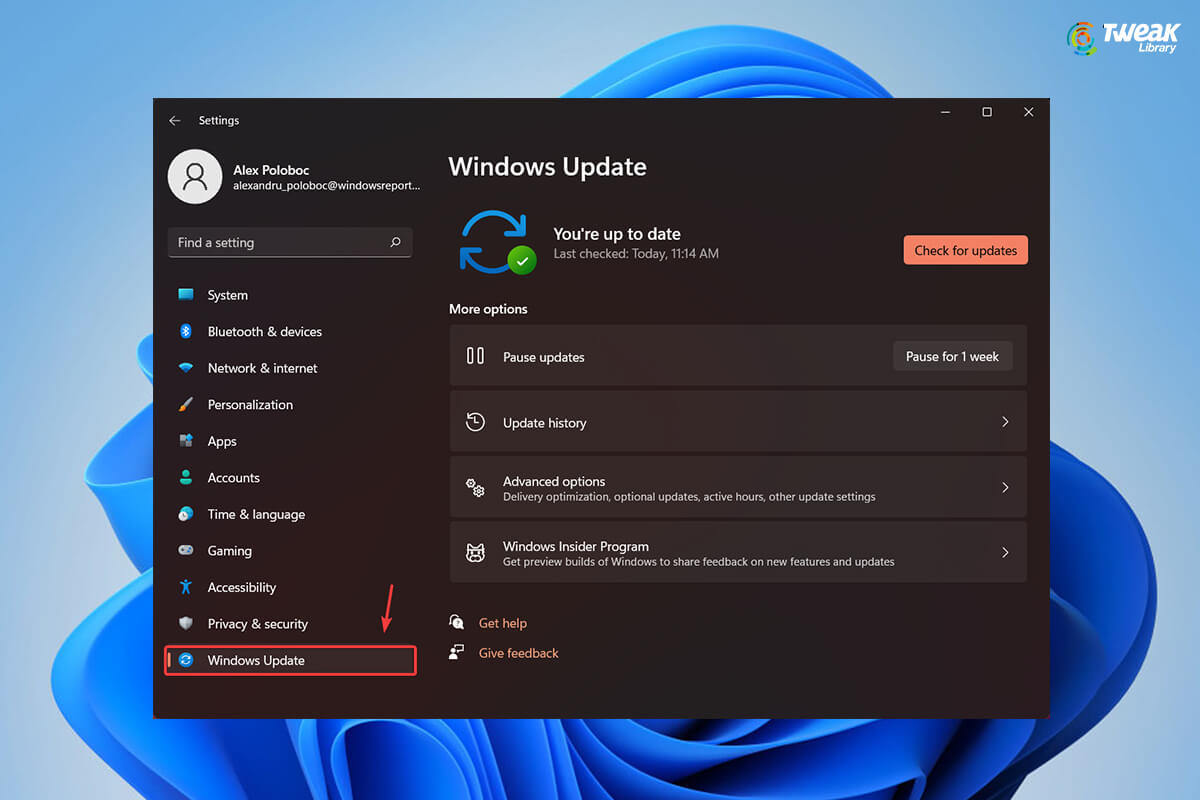
You might be using Windows Defenders as a prime shield against malicious threats. However, This shield may weaken if Windows Defender won’t update. ...

Often, when working on a Mac, we have to deal with folders that have similar names. Our first instinct at times is to bump heads with these folders an...

Under normal circumstances when you upgrade to Windows 11, all your files will be transferred automatically. However, in case of incompatible hardware...
Windows 11 launched and all the Windows enthusiasts were dying to get their hands on it. But wait ! Before you get that super cool brand new Windows 1...

Pandemic brought everything to a halt. People moved back to their hometowns. However, IT companies have accepted the Work From Home culture to keep th...