
Quick Access in Windows 11 is a feature that allows users to browse and access frequently used files and folders. This is a great feature that saves t...

Despite a working internet connection, many Android users have come across the Downloading English (US) Update Waiting for network connection error. A...

Want to free up disk space after updating to Windows 11? You are not alone. One of the reasons why this shortage in storage space might have occurred ...

Windows 11 is a new OS that is self-sufficient in resolving minor issues by updates and troubleshooting processes. As the OS is new many users are not...
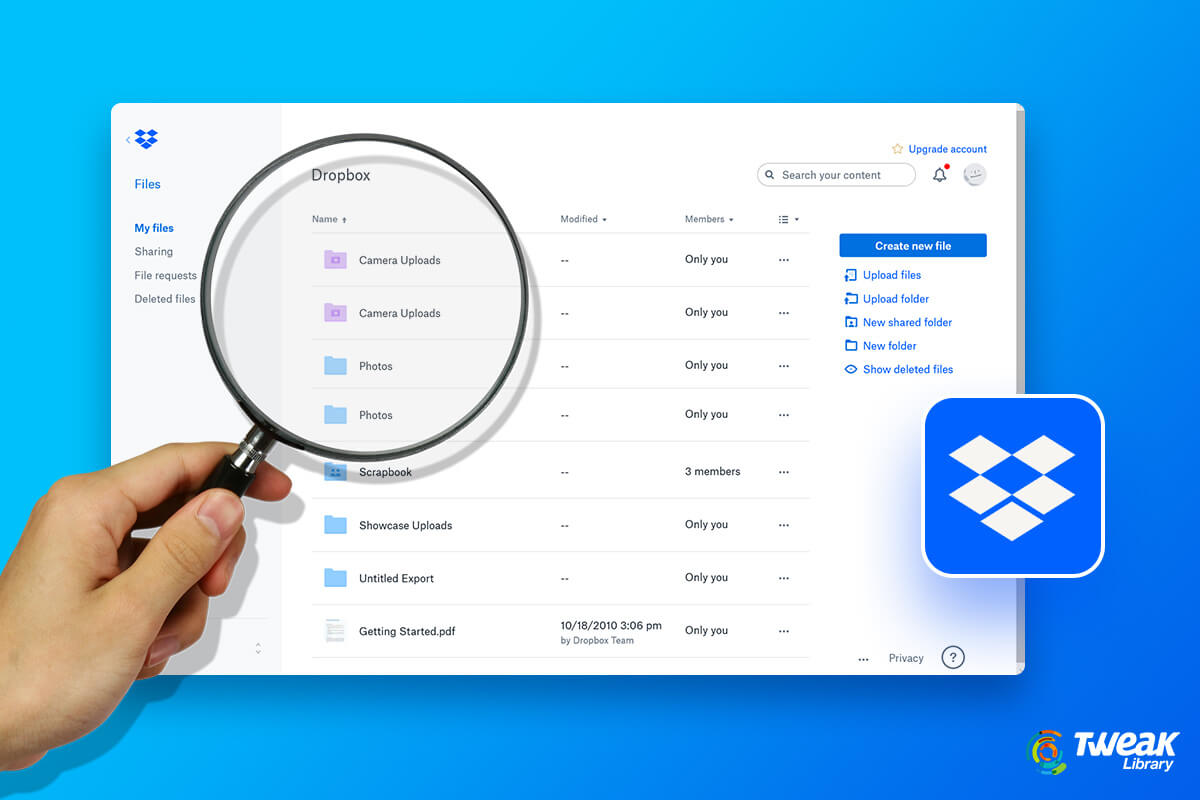
Dropbox is hands down one of the most popular file hosting services. It is used for business and personal use by almost 700 million registered users a...

Your password is that essential layer that can prevent someone from stealing your online and offline data and identity. It is for this reason that sha...

You have probably heard of the Zoom bombings where video conferences are disrupted by miscreants. That’s just one of the many camfecting incidents w...

Microsoft regularly rolls out updates that are essential from the standpoint of features as well as security. However, there have been instances where...

Laptops have all the components packed in a small space that helps you to do your work anywhere. However, this ease of comfort of doing the work has a...

Smartphones are often talked about in bad light despite being such an important part of our lives. From making calls to sending texts to using it as a...

Are you a gamer and want to improve the performance of your computer suddenly and surprisingly way? Well, you can do so by enabling Windows 10 feature...

Day in and day out, we store tons of data on our computer. There are documents, images, audio files, applications, and several different kinds of file...