Keeping yourself ahead of vulnerable threats is hard, but not understanding those technical jargons makes it even harder.
October is marked as the National Cybersecurity Awareness Month (NCSAM). As cyber-attacks have been on the rise for the past decade and show no signs of letting up. NCSAM is commemorating its 15 years this coming month since it’s raising awareness about the importance of cybersecurity. So, through our blog, we aspire to contribute to the same!
The guide is handy for the people who are not fluent in common cybersecurity terms and mostly find themselves lost in arduous discussions.
Before beginning with our most common cybersecurity glossary, let’s understand the two most widely terms.
-
Cyber Attack
Cyberattack is a deliberate action to exploit computer systems, tech-dependent enterprises, and networks. With the intention to harm, to damage, to breach information of an individual or organization- Cyber-attacks are attempted.
Remember- no company is too large, or home network is too small, to fall a victim.
-
Cyber Security
To simply put, cybersecurity is a protection against those cyber-attacks. Multiple security layers are spread across the systems, programs, and networks in order to keep individuals & organizations protected from unauthorized exploitation.
Though implementing effective cybersecurity shields is a challenging task today, and users should always be a step ahead to beat cybercriminals.

Most Common Cyber Security Terms
Learning these computer security terms will help you better understand the importance of digital security.
1. Adware
Adware can be defined as a bundle of programs that is designed to bombard users with advertisements. The main aim behind it is to redirect the user’s search requests to advertising websites and collect marketing data.
Adware tracks user’s online activity, slow down the device’s performance, displays customized ads and gets malware downloaded at the back end and also eats lots of data costs.
2. Botnet
A botnet is a bunch of several Internet-connected devices such as PCs, mobiles, servers and IoT devices that is infectious and controlled by a specific type of malware.
As the name suggests, it’s a blend of two terms, Robot & Network. And that’s exactly what they are, a network of robots that are used to commit crimes in the cyber world.
Here’s an anatomy of how Botnet works!
3. Clickfraud
Clickfraud happens when artificially created bogus clicks are used to manipulate Pay-Per-Click (PPC) advertising. The idea behind this practice is to increase the number of payable clicks, in order to generate revenue to advertisers.
Cybercrooks use Botnet to create these types of scams. Either this practice can be followed by individuals to manually click the AD hyperlinks or by using automated software or online bots to click these AD links.

4. Cyber Espionage
When you hear about Cyber Espionage, characters like James Bond might come to your mind, that pretends to be someone who they’re not, infiltrating organizations & also stealing secrets.
Similar to that fictional character, Cyber Espionage is the term that describes the practice of spying on someone to gain illicit access to confidential information. The prime target of this cybercrime is typically large institutions and government organizations. But it doesn’t mean individuals are too small to fall a victim.
5. Dark Web
With so much happening through the Internet, there is so much more in the World Wide Web than it appears. And Dark Web is that part of the Internet that is not visible to regular users. To understand what Dark Web is, first you need to understand what Deep Web is.
It’s a vast network of websites & portals that are not categorized by search engines. Likewise, Dark Web is just a small portion of Deep Web that has thousands of dark sites where all illegal activities are executed.
6. Defence-in-Depth
DiD is an approach used to create multiple layers of security to protect information resources/assets and valuable data in an enterprise from attacks. If somehow any mechanism gets fails, another security layer steps up immediately to thwart an attack.
No organization can remain secured with a single layer of security. Therefore, this multiple layered approaches to security is applied at each level of IT Systems.
7. Demilitarized Zone
The Demilitarized Zone is known as a firewall setting that separates LAN of an organization from the external network. DMZ makes certain servers available to everyone while keeping the internal LAN access private and accessible to only authorized people.
8. Detection Deficit
Detection Deficit is the gap between the times it takes to ‘Discover’ a breach from the time of ‘Compromise’.
9. Easter Egg
It’s a non-malicious surprise embedded in a program or media which is entertaining and accessible to anyone. It can be found in every software these days, especially in video games. It’s an intentional joke, hidden message or image usually found on the menu screen.
10. End-to-End Encryption
End-to-end encryption is a method of protecting and securing communication that hinders third parties from accessing data when it is transferred from one device to another.
For example, whenever you do online shopping using your credit card. Your mobile phone needs to send the credit card to the merchant. It’s End-to-end encryption method that just makes sure that only you and the merchant’s device can access the confidential credentials.

Also Read : Cyber Security Insurance: A New Age Scam?
11. Evil Twin
An evil twin is a fake Wi-Fi hotspot or access point that poses to be original and safe, but it’s actually set up to snoop on another wireless network.
12. Exploit Kits
Exploit Kits are basically the package of automated threats that are used by attackers to launch exploits against vulnerable programs. Exploits are designed to cause unexpected behaviors that an attacker can take advantage of to perform harmful actions.
13. Firewall
A Firewall is a defensive technology that is focused on to keep bad guys out from one’s network. It acts as a virtual barrier that protects both internal and external cyber-attacks that might attack your personal computer.
It keeps a check on all the unauthorized access to or from a private network and also determines which entry should be allowed or not to interact with your computer.
14. FTP
If you hang out with tech geeks or especially web developers, you might have heard FTP a lot. If you’re nodding, probably you know what it means. FTP is short for File Transfer Protocol that is meant for uploading and downloading files.
For instance, any two systems that use the same network can transmit files using FTP Protocol.
15. Gateway
The gateway acts as a bridge between two networks that connects using different protocols.
16. Guessing Entropy
It’s a measure of difficulty that an attacker has to guess in order to crack the average password used in a system. Generally, entropy is stated in Bits.
When a password has n-bits of Guessing Entropy, more the difficulty arises for an attacker in guessing the average password.
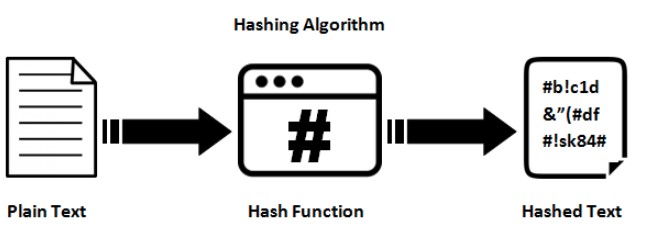
17. Hashing
Hashing is an encryption algorithm that converts the plaintext password into hashes. It’s a form of cryptographic security method that is used to transform strings of characters in shorter fixed-length value that poses as the original string.
For example: When a user wants to send a secure message, a hash is generated & encrypted to the intended message & is send along. When the message is sent to the end, the receiver decrypts the hash as well as message to read it.
18. Handshaking Procedures
The process by which two information systems establish a communication channel. Handshaking begins when one device sends content to another device for identifying, syncing, and authenticating themselves to one another.
19. Identity Theft
Sometimes also referred to as Identity Fraud, it involves the unauthorized taking of someone’s personal possessions and then using it in an illicit way for their own benefits.
20. IDS
Intrusion Detection System is software or device that functions to monitor network traffic for malicious activity. These detection systems help in identifying suspicious activity, log information related and attempts to block and report it.
21. IP Spoofing
IP Spoofing or IP Address Forgery is a hijacking technique in which a cracker pretends as a trusted host to disguise someone’s identity, hijack browsers, or gain access to a network. Though it’s not illegal to spoof an IP Address, as you’re just faking your address to hide your online activities and be anonymous.
However, if someone uses the technique to masquerades as someone else and indulges in criminal activities such as identity theft, then it’s illegal.
22. Keylogger
Often referred to as Keystroke logging, Keylogger is a computer program that keeps a log of your keystrokes on your keyboard. The entire log is saved in a log file which is encrypted and can be shared with different receivers for different purposes. It can be used for both legal and illegal means. It can track all the sensitive information like passwords and PIN (Personal Identification Number) in real-time and can be used for hijacking your personal accounts.
23. Macro Virus
A macro virus is a small piece of code which is lodged into the macros of different documentation and software programs such as spreadsheets and word documents. Whenever a user opens up the document affected with a macro virus, a series of actions begins automatically. The macro virus replicates rapidly upon sharing the document with multiple nodes.

24. Malware
Malware is a troupe of all the malicious programs like viruses, Trojan horses and spyware. It is a malicious program that reaches a target computer and runs the scripts which take the entire control over all the computing functions of the target computer. It can steal and hijack all the sensitive stored in encrypted files by decrypting them.
25. Mobile Banking Trojans
Users who are very frequent in using electronic gadgets for banking purposes are most liable to get affected by Mobile Banking Trojans. The influence begins with overlaying of Trojan’s interface over Banking app’s interface. When the user input their credentials to login into their account, Trojan loots them and impersonates user’s account.
Acecard family and Faketone Trojans were very effective in a cyber plague in 2016 which took over dozens of banking applications in Russia.
Must Read : Cyber-Kinetic Attack: A Reality Or Myth?
26. One-Way Encryption
Hashing and Encryption serve the same purpose, that is a secure transmission of data between the sender and receiver. The primary difference between both is that, in Hashing, you can’t reverse the process for retrieval of the un-hashed original string but in encryption, you can. Hashing is a kind of One-Way Encryption which is an irreversible process that’s why it is termed to be one-way.
27. Open Wi-Fi
An Open Wi-Fi network is an unprotected connection that doesn’t require any authentication to connect to it. Though for a layman it is a treat rather it is a threat to your personal information since you are exposing yourself to all the nodes connected within that network. Hackers can monitor all the entire traffic which is unencrypted.
28. Password Sniffing
Password Sniffing is the process of intruding between a transfer of data packets which encompasses password. The process is performed by a software application called Password Sniffer which captures the data packets which contains password and stores it for illegal and malicious purposes.

29. Pharming
Pharming is another malicious mechanism which redirects a user to a fake site falsely which appears to be a genuine one. A user enters all the credentials into the duplicate site considering it to be the legitimate one. Pharming is a sort of Phishing which has become a major threat to all the e-commerce and e-tailor websites.
30. Phishing
By Phishing, a hacker strives to steal your personal information such as passwords and e-mails. Phishing is done primarily through false e-mails that appear to be sent through a legitimate site such as Amazon or e-bay. The e-mail asks you to update or validate yourself by providing the username and password in order to read the information. Scammers then take the total control of your account and thieve your information such as bank account’s information etc.
31. QAZ
QAZ is a famous backdoor trojan that launches the untampered version of notepad.exe into systems, that allows hackers to link and gain access to the affected computer.
32. Ransomware
Ransomware can be any malicious software that encrypts data found on an individual’s or enterprise system. Once the data gets encrypted in wrong hands, the victim is demanded a huge amount of money i.e. ransom.
33. Reverse Engineering
Reverse Engineering is a mechanism for maintenance and improvisation of the software over time. It is used to find bugs and vulnerabilities in software by analyzing the underlying blocks of code. This mechanism also helps in reducing the replication of unintended code reducing the overall costing for testing and maintenance. Hackers and Crackers use Reverse Engineering to find the vulnerabilities in any Operating System.
34. Rootkit
The word Rootkit has been derived by two words, ‘root’ which means total control over the system or getting administrator rights by bypassing the authentication process and ‘kit’ means the set of tools like software applications and packages to undergo this intrusion for privileged access. Once the intruder gets total control over the system like that of an administrator, it can modify and delete the elements of software applications which is not otherwise accessible.

35. Script Kiddie
A script kiddie is a term used for the newbies in hacking and cracking. They don’t carry their own skill to write a script on their own, they use scripts developed by other hackers. It doesn’t require skill or experience to be a script kiddie.
36. Social Engineering
Social Engineering happens when a scammer manipulates a user into giving up their personal data. A social engineer is a man who interacts with individuals in order to gather their sensitive information and eventually rip them off.
The most common example of social engineering is when some attacker tricks users into giving their banking credentials and other transaction information.
37. Trojan Horse
Trojan horse is a malicious program that was first reported in 19744 in US Air Force report. The payload of this may be anything but, in many instances, it acts as a backdoor for the attacker. Once the attacker has control of the hosts system, they can lay their hands on the personal info like banking credentials or infect the network as well.
38. Vishing
This is yet another attempt of the attackers to get access to the financial details of a victim. Vishing or voice phishing is special because attackers try to do so via phone call.
39. Zero-Day
Zero Day is a computer software vulnerability which is unknown to security professionals but known to hackers. Before the concerned parties can detect and mitigate this, the hackers exploit that loophole.
Read Also: What Is Cyber Insurance And Why Do You Need One?
40. Zombie Computer
Zombie Computer happens when the remote-access Trojan horse leaves hidden codes into a system that allows a criminal to control the computer remotely. Attackers rely on various robot networks that help is creating zombie computers so that they can carry out crimes in the cyber world.
Regardless of what you understand and learn from this cybersecurity glossary, your mind has at least been opened to some new thinking today!






Leave a Reply