On Tuesday, March 19th one of the world’s biggest aluminium producers, Norsk Hydro fights ransomware attack.
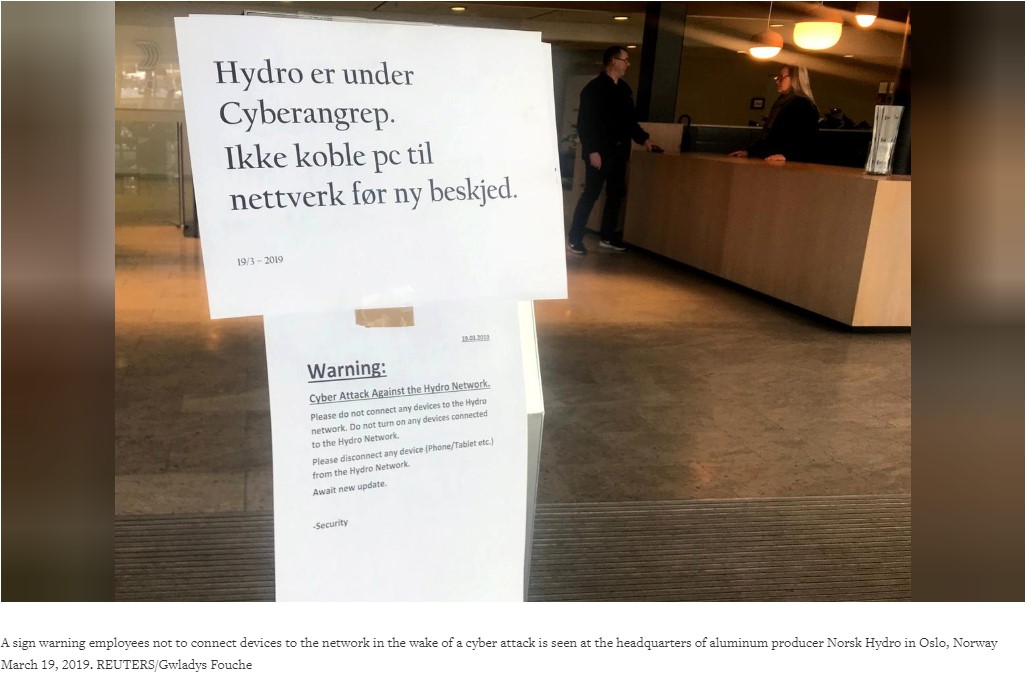
Due which company’s U.S. based plants, metal extrusions and other rolled product plants that changed aluminium ingots into gears, machinery for builders, car makers and other industries had to shut down. The situation is now under control, as company had good backup plans. Moreover, company switched operations of its oversized smelters in Norway to manual.
In a statement posted on Facebook company said: “Hydro is working to contain and neutralize the attack, but does not yet know the full extent of the situation.”
<blockquote class=”twitter-tweet” data-lang=”en”><p lang=”en” dir=”ltr”>They’ve informed stock market they’ve gone to manual operations. Anybody know what the deal is?</p>— Kevin Beaumont ??♀️ (@GossiTheDog) <a href=”https://twitter.com/GossiTheDog/status/1107928639612555265?ref_src=twsrc%5Etfw”>March 19, 2019</a></blockquote>
<script async src=”https://platform.twitter.com/widgets.js” charset=”utf-8″></script>
With this attack burning question like how ransomware enters into the company’s system, how it works, what is it called, what to do to stay secure stands up.
Answer of which is not hard to find.
As you read further you’ll get information about the ransomware, how it exploits the system and more.
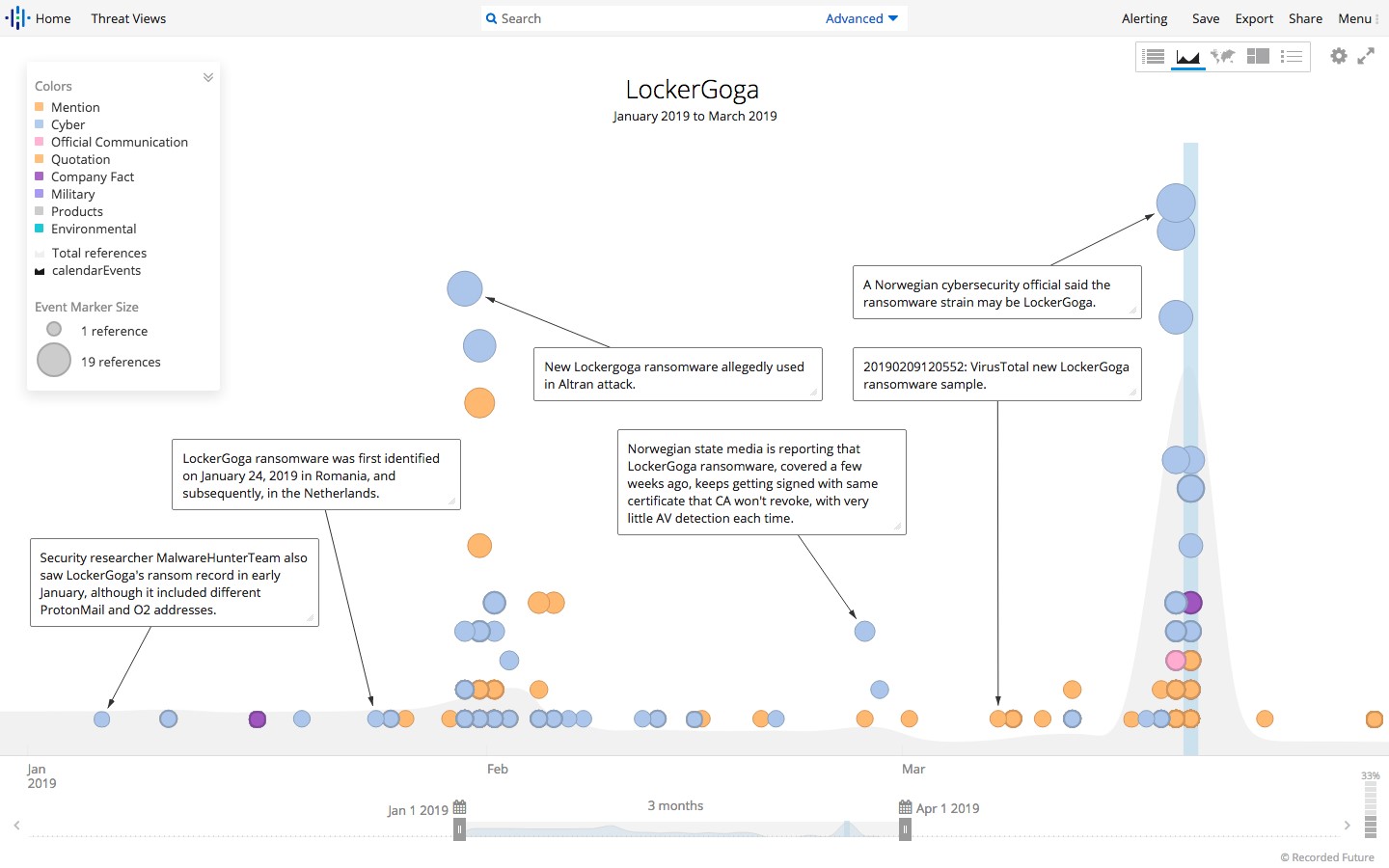
First thing first, according to the Norwegian National Security Authority (NNSA) attackers used ransomware called LockerGoga.
To deliver the ransomware to endpoints, company’s own Active Directory service was used against it.
This isn’t the first time that this ransomware has surfaced. LockerGoga was used to attack and extort money from French engineering firm Altran Technologies in January.
“LockerGoga is only used in limited targeted attacks. It does not have a ‘spreader,’ it’s not like WannaCry or NotPetya. It has to be deployed by an attacker who already has admin access,” Beaumont said via Twitter.
How were the attackers able to access admin sites?
These days getting access of admin sites is no big deal. Hackers use the most common approach i.e. they obtain brute-forced remote desktop protocol credentials from cybercrime markets. With the help of these credentials they easily enter into organization’s network, study it and raid the system for sensitive data, before even using ransomware for monetization.
What is LockerGoga and How it works?
LockerGoga is fairly a new strain of ransomware that encrypts computer files and demands ransom to decrypt them. This ransomware encrypts DLL files and is installed manually. Attackers behind it mostly use Active Directory to spread ransomware.

In case of Norsk Hydro it is suspected that phishing campaigns were used to spread LockerGoga. Plus, at the time of writing no decryption tool is available for LockerGoga. The best defence against ransomware is caution, observance against phishing attacks and to running updated antivirus and other endpoint protections.
How LockerGoga Works?
Attackers behind LockerGoga use classic approach i.e. malware encrypts files with targeted extension and then leave a ransom note as in case of Ryuk, SamSam
Once installed it alters user accounts by changing their passwords and tries to log off logged in users to relocate itself in the temp folder and rename itself via command line. Plus, LockerGoga also encrypts the victim’s Recycle Bin directory contents. Another interesting characteristic of this malware is, it encrypts each file individually and each file is encrypted following registry key is modified: (HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session00{01-20}.
Usually ransomware does not do this as overheads are created and it is an incompetent approach.
Plus, C&C, DNS beaconing, etc. are not added to the malware code, therefore assumptions are LockerGoga’s intentions are disruption, rather than spying.
After encrypting files, LockerGoga leaves following ransom note in a .txt file.
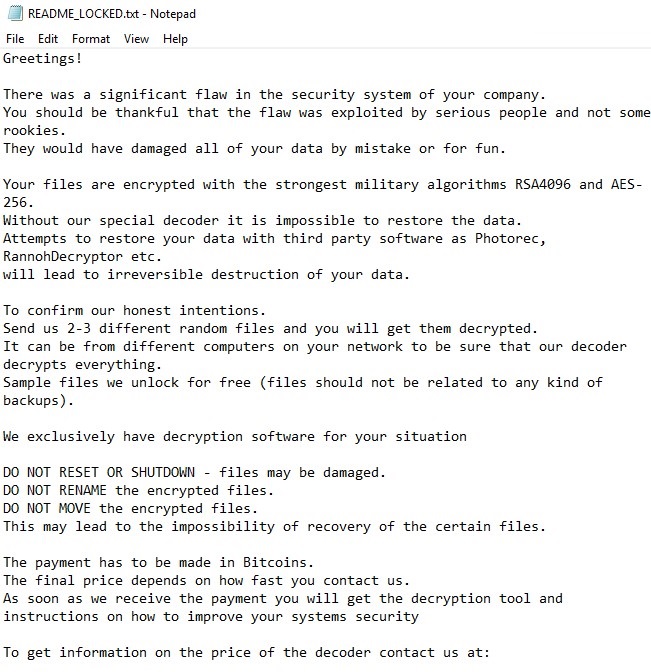

Besides this, another interesting thing about LockerGoga is the ransom note does not include wallet address for Bitcoin or Monero wallet. It simply includes two email address to contact malware distributor. Plus, to increase the probability of receiving ransom attackers offer to decrypt small number of encrypted files for free.
How to know if you’re infected with LockerGoga?
As the targeted files are encrypted and “.locked “ the file extension is added at the end of the filename, you can identify that you’re infected.
What do we learn from these types of attacks?
First and foremost, these troublemaking attacks do not target any specific segment. Individuals, companies
Also, paying ransom is not a solution, because the payoff will only help attacker to design more advanced malware. Also, knowing that they will be paid, criminal will be encouraged to attack.
Examples of devastating ransomware attacks:
NotPetya attack resulted in $10 billion in damages to supply chain companies
How to stay safe against LockerGoga
By following these certain practices, you can stay secure from ransomware like LockerGoga:
- Take regular backup of files and make sure it has working back-ups
- Always keep system, security applications and other software up to date. Plus, patch unpatched systems
- Implement data categorization and network segmentation to minimize exposure of sensitive data.
- Disable third party components as they can be used as entry points.
- Avoid uninvited changes in the system, implement additional layer of security like behaviour monitoring and application control
- Educate employees to implement security in the workplace. Plus, make them aware about ways to identify phishing and scam emails
Wrap Up:
Data is a treasured resource, for individuals, organizations and attackers. Whether it is an image or a corporate document all are valuable. Therefore, we need to protect it. Cybercriminals keep an eye on it to steal it and make money. One silly mistake from our end can lead to severe damages.
Frequency of ransomware attack over the last few years has increased, and it is not only used to generate profit it is also used to disrupt the operations of the network, and to hide tracks. LockerGoga being a new strain might be lacking sophistication, but it is another example of how a ransomware can cause damage when leveraged against an organization or individual. Therefore, be cautious and stay safe. To defend yourself from ransomware attack always take a backup of important data and keep system updated.
We hope you liked the article and would want you to stay tuned with us for the latest security news. Subscribing to TweakLibrary, by hitting the bell icon will help you receive notifications and stay tuned with us. Do leave us comment in the section below.




Leave a Reply