CryptoMix a ransomware that emerged in 2016 claimed to collect ransom to help children. Following footsteps of CryptoMix, Robin Hood a new strain of ransomware is creating havoc.
This new ransomware, Robin Hood uses reciprocity principle and other manipulation techniques to make victims pay ransom.
What Makes Robin Hood Ransomware Interesting?
Robin Hood ransomware ask victims to pay ransom for a different purpose. Its creators make some surprising claims about the ransomware and users’ privacy.
They claim to delete encryption keys and IP addresses after receiving ransom as users privacy is important for them.
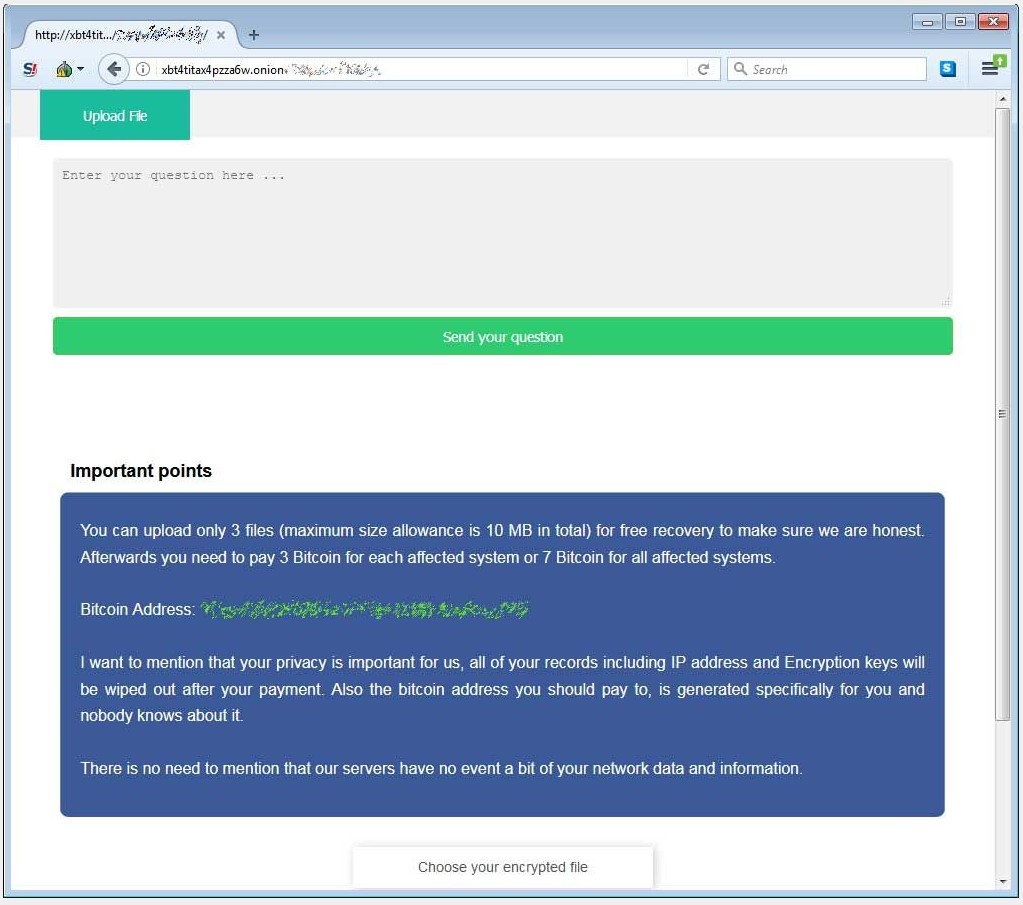
“Your privacy is important for us, all of your records including IP address and Encryption keys will be wiped out after your payment, ” Onion payment page mentions.
Another surprising claim about honesty, victims can upload upto 3 files maximum size 10MB and decrypt them to ensure developers are honest.
In addition to this ransom note further states that the amount will keep increasing to $10,000 each day if not paid by the fourth day.
Also Read : Future Of Ransomware In 2019 And Beyond
Remember: individuals should not fall for such gimmicks and should avoid paying ransom as it only boosts cybercriminals confidence to create more such attacks. Also, there’s no guarantee that creator will give back the files after paying ransom.
RobbinHood targets entire network and encrypts data to gain access. After that threat actor requests victim to pay ransom in bitcoin to decrypt data.
How Robin Hood Ransomware Work?
Not much information is available about Robin Hood ransomware. However, it has been found targeting computers within a network. Plus, once installed Robin Hood will encrypt files to something like
Encrypted_b0a6c73e3e434b63.enc_robinhood.
Soon after this, 4 ransom notes are left with following names:
_Decryption_ReadMe.html, _Decrypt_Files.html, _Help_Help_Help.html, and _Help_Important.html.
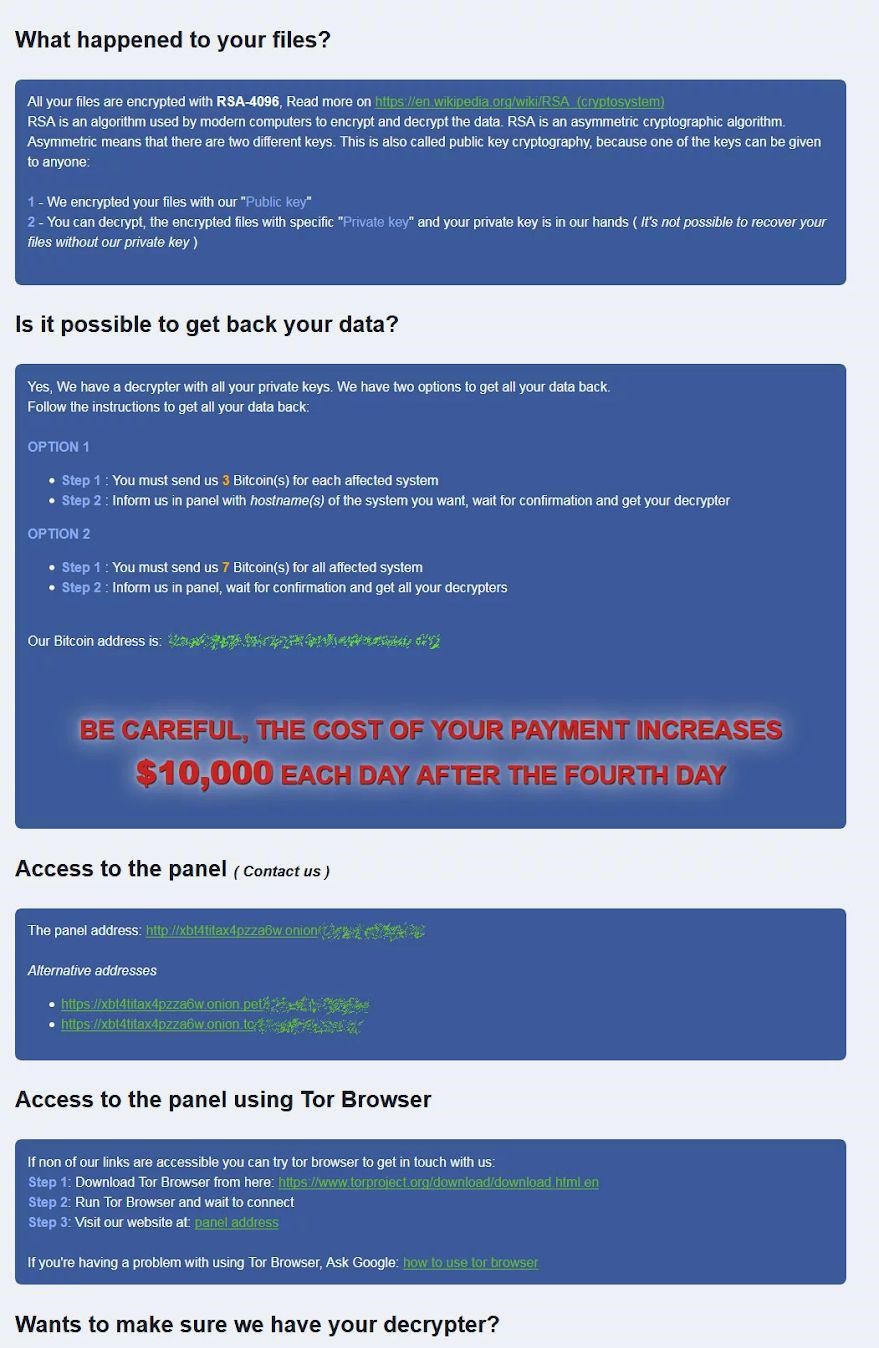
What these ransom notes say – The ransom note comprises of information related to ransom amount, TOR sites and what happened to files.
Using TOR links victim can drop a message for the attacker to get 3 files decrypted of up to 10MB in size without paying.
In addition to this, ransom differs on the basis of computers that are encrypted.
Must Read : HOPLIGHT: North Korea’s Another Attempt At Becoming A Hacking Regime
RobbinHood keeps Privacy Intact
What’s more interesting, Robin Hood states that victim’s secret is safe and there’s no need to involve police or government authorities.
This practice is done to get victims pay ransom and get their data back.




Leave a Reply