If you have robust Antivirus protection, a cybercriminal sitting at a remote location too is cooking some or the other tactics to bypass it. And, several instances have happened where malware and other malicious threats went undetected by even the most robust Antivirus application.
Glimpse of DangerTake, for instance, a new strain of Windows malware – Tardigrade. It can constantly adapt to avoid detection. And, it is not something that exists in theories. The malware has been found attacking the biotech industry which includes the infrastructure behind vaccine manufacturing. The malware completely recompiles its code with each infection. Its metamorphic ability makes it next to impossible for Antivirus to detect it since it does not leave a consistent signature behind. |
And, this is just one of the many examples or rather ways malicious threats have been known to bypass Antivirus programs. The intent of this blog is not to scare you, but to first, make you aware of the ways malware and other malicious threats are known to bypass Antivirus applications, and second, what kind of Antivirus should you use to keep even the most sophisticated and powerful threats at bay. Also, what measures you can take to not invite them in the first place.
How Does Your Antivirus Identify Something As A Malicious Threat?
In simple terms, an Antivirus is told – what is a virus and what is not. Actually, it is not this simple. The developers who create an Antivirus take into account even the most modern, most sophisticated, and the latest malicious threats. They then provide these updates (definitions rather) to their Antivirus program. Once that happens, an Antivirus has a template of what it can identify as a threat and what to not identify as a threat.
Also Read: Can An Antivirus Slow Down Games On Your PC?
Getting Into The Shoes of A Cybercriminal
How on Earth can a cybercriminal create a malicious threat that can go undetected by an Antivirus application. Actually, these miscreants have developed a range of techniques that can bypass the functionality of an Antivirus. There are ways more than one where computer viruses go undetected. Let’s discuss some of these techniques briefly.
– Stealth Techniques
The technique does what it reads, the virus such as a Rootkit goes into a stealth mode. The virus intercepts system functions and replaces itself with a clean file. Even at a registry level – the threat’s registry branches and other system files are hidden because of which it becomes nearly impossible for an Antivirus to catch hold of the virus.
– Zero-Day Threats

There are times when we see our Antivirus program updating frequently and get irked. Don’t! Since your antivirus might be preparing for a Zero-day threat.
This is a technique where a cybercriminal exploits a software/ hardware vulnerability and then releases malware before an Antivirus program can patch it.
We have talked at length about how you can fix zero-day vulnerabilities in this post.
– Code Packing and Encryption
One of the ways cybercriminals make a virus hide from Antivirus software is by the means of code packing and encryption. As the name suggests, the maker designs special utilities to pack and encrypt malicious threats such as Trojans and worms. To combat such attacks, an Antivirus application should be powered with new decoding and unpacking methods or new signatures of each sample of a malicious threat should be added.
– Block Antivirus Database Updates and Programs

Here the virus directly locks horns with your Antivirus. It tries to damage its databases, blocks the software per se or even hinders the Antivirus update process.
– Quantity Attacks
Here the intent of an attacker is to distribute large quantities of Trojan versions across the world wide web. Why would they do this? In the hope that, till the time the various Antivirus companies will analyze and find a way to combat the virus, the malicious code will get a fair chance to penetrate the computer of various users.
– Masking Codes On A Website
Antivirus companies are prudent and smart and are timely able to identify all websites that host malicious files. But, what if a smarter cybercriminal modifies a webpage in such a manner that when an Antivirus company sends requests, they end up downloading a non-Trojan file instead of a Trojan file.
How Can You Combat Viruses At Your End?
When an Antivirus can’t, how can I ward off a malicious threat? What if we said, you certainly can, by practicing some preventive measures. First and foremost, don’t refrain from installing a good Antivirus program on your operating system. Systweak Antivirus, for instance, is one of the best Antivirus for the Windows computer. Let’s first have a look at some of its features –
- Scans every nook and cranny of your computer for malicious threats
- Systweak Antivirus comes armed with active web and firewall protection
- Exploit Protection helps defend against threats that exploit your PC’s vulnerabilities
- Its database of malicious threats is frequently updated
- Unlike many of its counterparts, it is light on your system’s resources
- It offers real-time protection against a variety of malicious threats
- Can fight off zero-day threats with a high success rate
- It offers multiple scanning modes i.e. Quick, Deep, and Custom scans
How To Use Systweak Antivirus?
1. Download and install Systweak Antivirus
The Complete Review of Systweak Antivirus
2. From the left-hand pane click on the magnifying glass icon
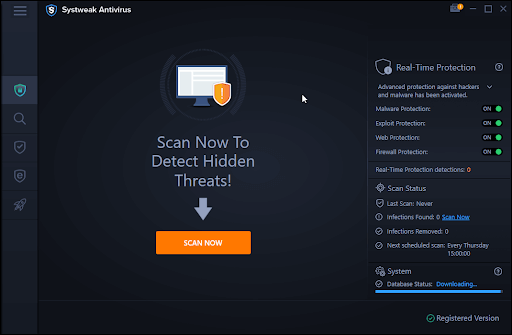
3. Choose the mode of scan and start the scan
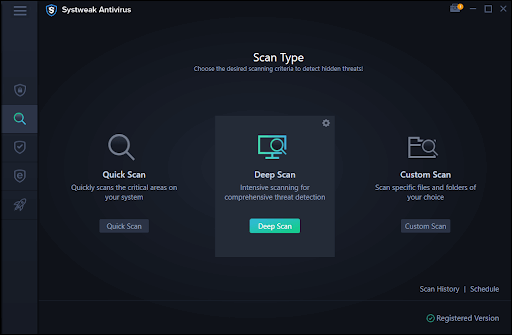
That’s how easy it is to use Systweak Antivirus.
Other Preventive Measures To Combat Malicious Threats –
- Keep your eyes and ears open for any security vulnerability in an app, software, or even in your operating system
- A second opinion can be an added shield. Even if you have your trusted Antivirus on your laptop, computer or smartphone, substitute it with an additional from your operating system’s ingrained security program. For instance, you can use Windows Defender as additional protection. This way even if a malicious threat surpasses one security program, it is very unlikely that it will even bypass the second one
- Never ever download a file from a suspicious source or website
- Even if you have mistakenly downloaded a file (supposedly infected) from a suspicious source, please don’t click it open
- Immaterial of what operating system or device you have Windows (laptop, computer or tablet), macOS (PC or MacBook), Android (all devices), iOS (all devices), Linux, Ubuntu, or any other operating system under the sun, make it a point to fetch regular updates. That’s because each update lets you patch security vulnerabilities
- Always keep applications on your computer or smartphone updated
Wrapping Up:
Now that you have a fair idea of how viruses bypass Antivirus protection, first and foremost be very cautious of the websites you are visiting and the files you are downloading. And, as we said, keep at least two Antiviruses so that by no means, a malicious threat causes damage to your system.







Leave a Reply