Nearly all browsers and websites offer to save your personal data to save you from the hassle of refilling the credentials every time. Generally, users tend to agree to save their details such as login id, passwords, credit card numbers, etc. on the browsers or Websites.
Apparently, this habit is really appreciated by hackers, especially Browser Hijackers. Before we continue to look at the reason why hackers are such big fans of these people, let’s first try and understand Browser Hijacking.
What is Browser Hijacking?
Although the name itself is pretty capable of explaining its meaning, let’s elaborate it a bit. When the people with malicious intent, hackers, try and get the control of a user’s browser, it is known as Browser Hijacking.

Contrary to a typical PC user’s belief, the web browsers that we use hold a surprisingly large amount of data related to us. From user-id, passwords, and credit card information to our location, work schedule, our topics of interest, etc., everything is stored in the web browser that we use. The sudden increase in respect or fear that you have for your browser is understandable.
But hacking a browser isn’t that easy as well. Especially with all the safety measures that browsers employ to safeguard user information.
What about the Browser Security?
All the admirable browsers in the market employ various techniques to safeguard users’ information from malicious attacks. Browsers also do not save the user information in plain text. All the user information such as IDs, passwords, etc. is stored in encrypted form which can only be decrypted by the valid user and from the authorized devices only.

So, it would be untrue to say that browser security is a myth. Then, how do hackers misuse the information stored on the browser?
How does Browser Hijacking work?
As we discussed, the critical user data stays encrypted in the browser and can only be decrypted by authorized users only on authorized devices. But the browser assumes that your system is protected and doesn’t need verifying. Hence, data can be accessed by an intruder with your identity.
To put it simply, when someone else from your device demands the information, the browser assumes no reason to doubt your identity. Hackers don’t need to use your computer in order to mimic your identity, a malware can simply do the task for them. Malware is programmed to fetch data from the browsers by Browser Hijackers. Malware keeps sending the fetched data back to these cyber-criminals.
How can the stolen information be used to harm you?
If the stolen information includes your social account details, these accounts can then be used in all kinds of illegal activities such as laundering, sending threat mails, spams, etc. You may lose access to all the information that was stored in the account including important files and pictures.
If the stolen information consists of your bank details such as credit card information etc., the loss can be more direct. Your money can either be used in some online transactions or can be transferred to some other account.
How to protect yourself from these Hijackers?
- One shouldn’t trust the browser on his/her personal information. Instead, IDs, passwords, and bank details should always be entered manually.
- The most popular method used by hijackers to get into your PC is Malware. One should always protect his/her system with a good antivirus. One of the most popular antiviruses that provide the all-round protection viruses, malware, spyware, and more is Systweak Antivirus.
- Users should always keep their browser updated for better protection from various threats.
Web Browsers are home to tons of critical user information. Hence, are an obvious target for hackers and hijackers. One should take decisive steps to safeguard such information.
In 2020, one has multiple accounts on different platforms and websites. Keeping track of so many passwords can be a daunting task. In addition to that, the chances are that you already have a lot of information stored on your browser already. So where should you start to safeguard your information?
Advanced Identity Protector:
Advanced Identity Protector is one of the best identity theft protection tools available in the market. It helps secure your personal information ranging from ids, passwords, credit card information to your location, work schedule, etc.

Advanced Identity Protector is equipped to scan all the unsafe files and information on all the different browsers installed on the PC and protect them. Let’s look at some of the most highlighted features of Advanced Identity Protector:
Click Here to Download Advanced Identity Protector
- Automatic Scanning and Securing: Advanced Identity Protector features automatic scanning and protection. When you install the Advanced Identity Protector for the first time, it scans all the unsafe information be it an ID, Password, Credit card information, or file.
With just one click, one can move all the information left unsafe on your browser to Advanced Identity Protector.

- Vault for Sensitive Information: You can easily safeguard your credit card details, account numbers, passwords, etc. into the vault and can access them when needed.
- Accessibility: Information saved on one device can be easily synced to other devices to provide access to information wherever you need it.
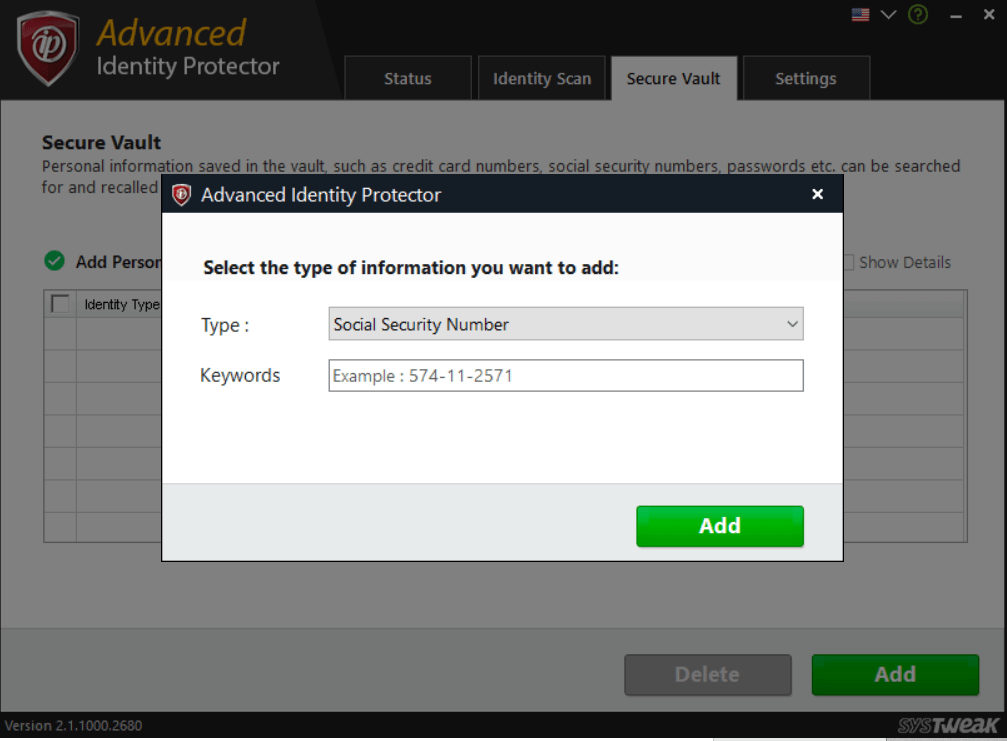
All the information stored on the Advanced Identity Protector is protected with the help of a Master Password. Therefore, with Advanced Identity Protector installed on your device, you only need to remember 1 password. It works as a Password Manager to eliminate the need to save your passwords and credit card information on the browser and different websites.
Next Read:
How do Firewalls Work to Ensure Network Security?
Spectacular 1Password Alternatives You Should Have







CHTN
Amid all the cyber scams, data scandals, & no-internet-security, the info above is extremely helpful & up to the point.