
Whether you are buying an iMac or iPad, besides hardware failures and manufacturing defects, you need to know that Apple offers complete one-year wa...

Among all other nifty features, Remote Desktop and Remote Assistance are two important features that allow us to connect to a system that is at a remo...

We all are familiar with Android and iOS platforms as both are popular but are quite different when it comes to functionalities. When we talk...

Smart speakers are dominating the smart home market. One in six Americans use either Amazon Echo or Google Home. These speakers not only perform diff...
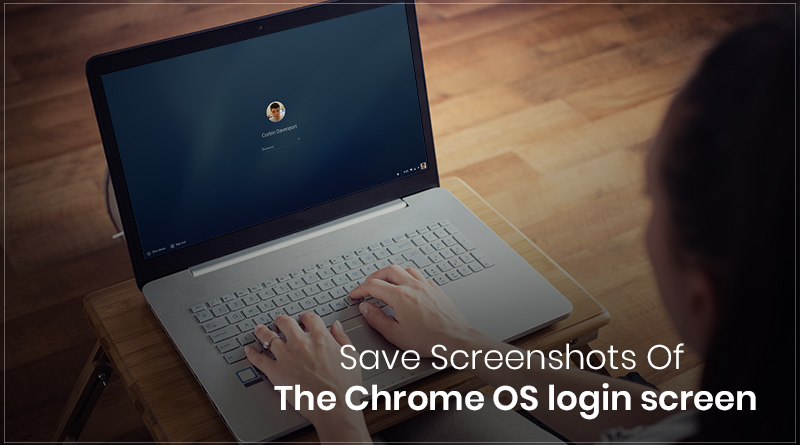
Taking a screenshot of a login screen on Chromebook seems to be a tedious task. People often do it for various reasons. If you ever want to do it, it...

Computers in today’s world have been upgraded with Smarter Operating Systems and advanced hardware. Yet slow performance and sluggishness still re...

Susceptibilities in Internet browser aren’t rare. As a matter of fact, major and minor updates released now and then include security patches, fix...

The web today is full of websites offering services to give out your information to others. These details can be obtained for free or by paying a sm...

The era when we used to know who we’re trading with is long gone. These days as a major part of our lives is spent online falling into the trap of i...

The more someone knows about you, the more vulnerable you are! Personal data plays an important role in knowing about a person. If the personal data i...

We have been reading a lot about computer viruses, malware, and other threats. And now out there is a new menace called Stalkerware. An invasive progr...

Do you suffer from clicking anxiety? The feeling you get before taping any fishy link on the Internet. You get surrounded with thousands of thoughts, ...