
Keep things distinct on Google Chrome and Firefox by using multiple profiles, here how to do it. One of the most appreciated features of Goog...

Smartphone issues are some of the most aggravating problems these days. Those errors could be intrusive and solutions aren't always easy to come by. ...

Mobile Hotspot feature in Windows 10 has been around for a few years now, and it’s definitely one of the most valuable functionalities that are wor...

When you try to print a document but are unable to do so as you receive: Windows cannot connect to the printer. The local Print Spoole...
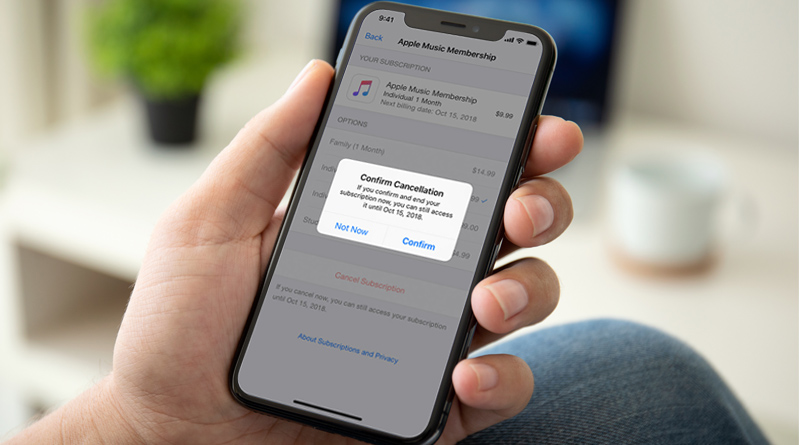
Apple’s App Store offers a plethora of apps with in-app purchase. As nothing comes for free, you need to purchase apps to get the best of the apps ...

When it comes to Android or iPhone we are quite familiar with the feature, “Find my Device”. However, do you guys know that this feature is not l...

Believe it or not, but streaming services have entirely changed the way we all consume media. Some people might be skeptical about the advantages of...

When it comes to email, Gmail is one of the most trusted and authentic platforms we can rely upon. Gmail happens to be a renowned email service offer...

Liked an article or picture you came across while browsing the internet on your Chromebook? You can save the page or image and keep it. However, som...

Whether you are buying an iMac or iPad, besides hardware failures and manufacturing defects, you need to know that Apple offers complete one-year wa...

Among all other nifty features, Remote Desktop and Remote Assistance are two important features that allow us to connect to a system that is at a remo...

We all are familiar with Android and iOS platforms as both are popular but are quite different when it comes to functionalities. When we talk...