At the beginning of each year, we see articles predicting trends about ransomware, malware and other attacks. Each being a mix of correct and incorrect predictions. In 2018 Ransomware was considered as one of the biggest malware threats, which by year-end started to fall out of favor as cybercriminals started to focus on cryptocurrency mining.
But this doesn’t mean new ransomware variants were stop being developed. They are still emerging and with this, we can say ransomware threat is not going away anytime soon.

Ransomware turnkey business for cybercriminals.
SamSam ransomware was one of the biggest ransomware attacks of 2018. The city of Atlanta was traumatized by it, as it disrupted business operations, daily lives of individuals, leaving some data completely unrecoverable. This is just one example there were dozens of other ransomware attacks that affected business, healthcare industry and government organizations in 2018.
Well ransomware landscape became diverse – till now security researchers have tracked over 1,100 different ransomware variants. This number keeps on growing and ransomware attacks continue to challenge different organizations.
10 biggest ransomware attacks you should know about in 2024
1) Bad Rabbit
The two large scale ransomware attack WannaCry and NotPetya made way for the third strain of ransomware. This new ransomware is called Bad Rabbit, Easter European organizations primarily based in Russia and Eastern Europe were infected by Bad Rabbit ransomware. Moreover, this ransomware spreads through drive-by download, it doesn’t use exploits.
Bad Rabbit ransomware disguises as Adobe Flash installer. Once the fake installer is downloaded from an infected site, it locks down the computer and demands a ransom. Sites using JavaScript are infected by Bad Rabbit ransomware. To get the system back victim needs to pay a $280 in Bitcoin within 40-hour deadline.
2) Cerber
Cerber ransomware is ransomware-as-a-service (RaaS). This means anyone can buy Cerber license online and release it in exchange for splitting 40% percent profit earned from ransom with the developer. This ransomware uses RSA-2048 key for data encryption, making it the most dreaded ransomware.
Once Cerber ransomware is installed it creates a random executable in %LocalAppData% or %AppData% or folder. It then scans all drives to encrypt files and adds .cerber extension to each encrypted file. Further, Cerber ransomware targets cloud-based Office 365 users, using a detailed phishing campaign. Till now this ransomware has infected millions of users across the globe.
Cerber creators, send infected Microsoft Office documents as an attachment. Once downloaded and opened Cerber ransomware starts to work silently in the background.
To decrypt data, the victim needs to purchase a special type of software. This ransomware asks the victim to pay a ransom in Bitcoin, within 7 days. Failing to do so the amount gets doubled.
3) Dharma
Dharma the new ransomware variant is a cryptovirus. Like other ransomware, it asks the victim to pay ransom for the decryption key. Attackers who exploit Remote Desktop Protocol services via TCP port 3389 deliver Dharma ransomware manually. To encrypt files Dharma ransomware uses AES 256 algorithm since 2016 15 variants of Dharma ransomware has been released. The latest version of this ransomware includes attackers email address and it includes file extensions .gif. AUF, .USA, .xwx, .best, and .heets. The spread of new Dharma variants clearly shows the wider distribution of the ransomware to new groups of hackers.
Also Read : Dharma Ransomware: Another Ransomware Returns From Oblivion
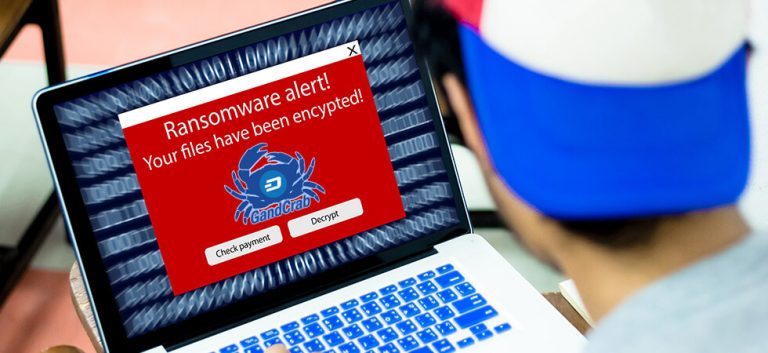
4) GandCrab
GandCrab ransomware discovered in 2018 like Cerber ransomware, is part of Ransomware-as-a-Service (RaaS). It is the first and one of the few ransomware that demand ransom in form of DASH cryptocurrency. GandCrab’s team rely on PowerShell, Microsoft Office macros, VBScript, to avoid detection.
Earlier versions of this ransomware used RSA and AES encryption techniques whereas version 4.0 of GandCrab ransomware uses Salsa20 as it is quick. Plus, GandCrab checks the system’s language to identify if payload can be dropped or not. Machines having Russian language or other former Soviet languages are skipped.
This ransomware has been constantly evolving and is the leasing ransomware threat for both businesses and individuals. The team behind this ransomware keeps on updating it to make it more devious.

Must Read : New GandCrab v5.1 Ransomware With Additional Features
5) Jigsaw
Jigsaw ransomware created back in 2016, was initially titled as “BitcoinBlackmailer” but due to the image of Billy the Puppet from Saw horror movie formed the name Jigsaw ransomware. This ransomware not only encrypts user’s files but also gradually deletes them. This means the victim needs to pay the ransom within 24 hours. As ransomware started deleting files every hour, more delay means less are the chances of data recovery.
6) SimpleLocker
SimpleLocker also is known as Andr/Slocker-A is a Tor-enabled ransomware that targets Android OS. It spreads through a Trojan downloader disguised as a genuine application. Once installed SimpleLocker scans the device for different file types and uses AES to encrypt files. SimpleLocker changes file extension to .enc and it collects information like IMEI number, device model, etc, all these details are then shared with a C2 server.
7) LockerGoga
LockerGoga a nasty new breed of ransomware that targets industrial and manufacturing firms, instigates substantial harm. After infecting Altran (French engineering consulting firm), it attacked Norsk Hydro and two other major US-based chemical companies.
LockerGoga ransomware the latest strain of malware is disruptive, shuts down computer entirely, lock out users making difficult for the victim to pay the ransom. This ransomware is named LockerGoga by a security research group. How this ransomware gains access to victim networks is still a mystery. However, some security experts say attackers already know targets credentials and this helps them to attack.
8) PewCrypt
Unlike other ransomware, this one is not created to make money. It seems PewCrypt creators have other goals in mind. This latest ransomware was created with one aim i.e. the author wanted victims to subscribe to YouTuber PewDiePie and help him reach 100m subscribers. This ransomware is coded in Java and it encrypts files in such a manner that they can be decrypted later. The catch is data will be decrypted when PewDiePie gets 100 million followers.
PewCrypt is distributed via spam email message. Initially, individuals considered it as a joke, but it did infect few users. Later the creator due to the fear of being caught released ransomware’s source code at GitHub with a command-line-based decryption tool.
9) Ryuk
Ryuk a targeted and well-planned ransomware that debuted in August 2018 since then has made $3.7 million in bitcoin. This ransomware is distributed systematically through massive spam campaigns and exploits kits. It uses AES-256’ and RSA4096 encryption technique to target small scale operations.
Security researchers thought Ryuk ransomware is connected to North Korea as this ransomware’s code is based on Hermes ransomware. However, later researchers determined that Ryuk is in Russia and it is built on stolen Hermes code.
10) SamSam
SamSam ransomware is most likely used in targeted ransomware attacks. It is often deployed using brute force attacks or a wide range of exploits. This ransomware has attacked a wide range of industries in the US and other countries.
The group behind SamSam ransomware (Ransom.SamSam) continues to attack targets located in the U.S. This ransomware breaks into the network and encrypts multiple computers across an organization. SamSam group’s modus operandi is to gain access to the organization’s network and spend time in mapping out the network before encrypting data. This ransomware continues to pose a grave threat to the organization in the U.S. A successful SamSam attack is disruptive as the data encrypted by it can be permanently lost after the attack.

Ransomware is avertible!
Although using a decryptor is some cases victim can recover data but there is no surety about it. The new variants of ransomware created each day are disruptive. Therefore, the best way to handle a ransomware attack is to backup important data. For this, we can use a backup tool that allows uploading data on the cloud. If you are interested and looking for one such tool, try using RightBackup.
This amazing cloud backup tool is loved by millions of users as it offers various features. After using this tool, you’ll no longer need to worry about your data. If you become a victim of a ransomware attack, you’ll still be able to use your data as it will be stored on the cloud.
We hope you’ll keep in mind, your data is not only important for you, but it is for cybercriminals too. Do leave us a comment to share your thoughts.





Leave a Reply