At present, advanced technology majority of the individuals are dependent upon the computer for almost everything, be it reservation, education, shopping or even banking.

Working over PC sometimes disturbs you and make you irate because of the unwanted pop-up advertisements emerging on your computer’s screen. The activities are frequently tracked at your system and bother your privacy due to the superfluous guests.
Consequently, PC performs slow or even hangs as well as the software’s without giving any prior notice crashes down, the browser homepage is hijacked, and you receive random error notices.
A harmful spyware generally affects the computer because of the various activities performed by the users, including: –
- Clicking onto the tab at the pop-up window
- Installation specific software
- Allowing adding additional functionality onto the browser
Spyware generally is installed in the PC by trickery. For example, a fraud system alert might feature a tab known as cancel for denying the request, but once you clink cancel, automatically the spyware gets installed at your computer.

Also Read: GhostDNS: The New Malware in Town
Few common methods through which the spyware can easily get installed on your system are: –
- Drive by download: In cases like these, the pop-up window or the website itself installs as well as downloads the contagious spyware on the system. If you possess accurate security settings in your system, then the browser will show a message mentioning the software’s name to be downloaded that might be malicious.
- Browser add-ons: The browser add-ons are meant to include enhancements like a toolbar and even animated pets onto your browser. When installing such add-ons, customarily some spyware elements gets installed onto your system. These add-ons are generally referred as the browser hijackers.
- Piggybacked software downloading: Many a times, spyware gets installed as a standard installation process of several applications. For instance, the peer to peer file sharing. Although the spyware is enlisted in the list of installation, but the user does not take account of it, basically because of less attention. This generally happens in the case of free versions that are advertised as alternative with the software you wish to buy.
- Posing as anti-spyware: It is the wicked method within which the spyware gets installed on the system. The software persuasively shows itself as the anti-spyware, especially meant to remove and detect spyware, when installing the extra spyware onto the system. While you run an application then it will state that the PC is clean and thus it is tough to detect and eliminate such software’s.
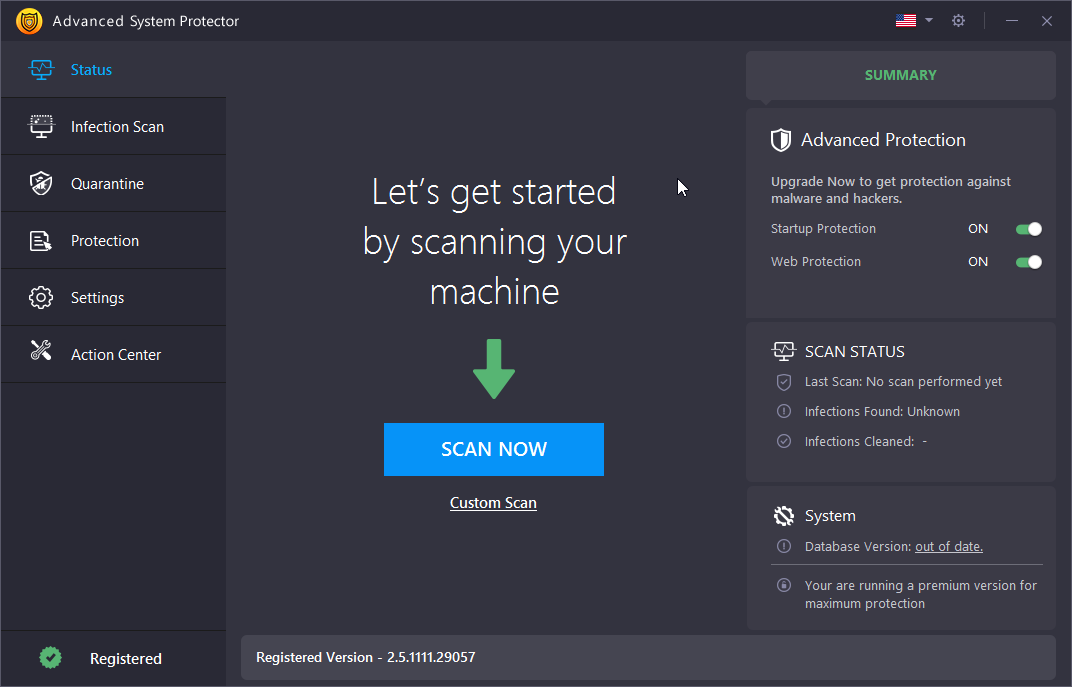
Luckily, anti-spyware or antimalware software comes as a rescuer in situations like these. It is one of the best solutions for securing your computer and enabling it to perform well. The antimalware makes you simply rest down and relax through protecting your system from all the possible unwanted and disturbing intruders.
It will properly check and scan your system for viruses and assist to remove it. Once the detection procedure or scanning is finished, all the reports stating the spyware threats will be displayed and immediately, the deletion process will be started. Therefore, using an antimalware is the wisest way to stop spyware writers from peeking into your systems.
Must Read: Hacks To Protect Customers Data From Cybersecurity Threats
Advanced System Protector is an amazing antimalware tool that is created to detect all types of malware threats and remove them instantly. Be it adware, spyware or sophisticated crimeware like phishing kits or browser hijackers, Advanced System Protector removes them completely. Other than keeping you safe from malware threats, it also has different features like managing startups, browser cleaners etc.
Want to download Advanced System Protector? Click on the button below-







Leave a Reply