In the world of technology, where any security wall can be breached using codes or loopholes, the SIM Swap attack isn’t surprising. Just sit back and think once about the number of apps and platforms that have your phone number to verify the identity. Got goosebumps? I did.
The two-step verification or two-factor authentication initiative has become a topic of meme throughout the world leaving many users its victim.

The more companies tried to tighten the security with additional security layers, the easier it became of attackers to make it a target. A security measure adopted by almost every service company has become a part of jokes with serious implications.
Even public figures like Twitter CEO Jack Dorsey had a hard time dealing with this.
Click to Tweet SIM Swap attack
What is The SIM Swap?
SIM swap (also called SIM swapping/SIMjacking/SIM splitting) is actually a breach that gives the attacker your account access. To make it understand in steps:
I believe you all now the two-step verification we go through while logging in to Gmail or any bank service platform. After putting a password, we either get an OTP or a call on the registered mobile number and that’s where the breach takes place.
In between inserting the 1st step password and then 2nd step OTP, the breach actor plays with a few codes and takes over your mobile number to his/her SIM card.
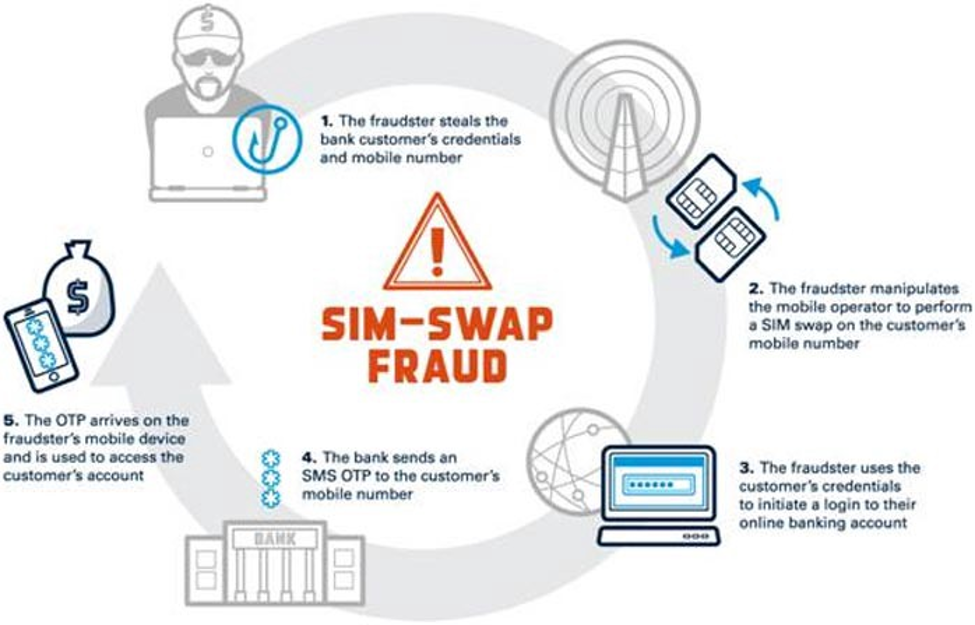
This results in getting the 2nd step password on their SIM card instead of the actual user’s and they get access to your account. Boom!!!
These types of attacks weren’t much before, however, in the last few years, it’s been happening repeatedly. The time when cryptocurrency came into existence for the transactions, the hackers got more active and there were reports almost every month for one or the other incident.
SIM swap attack is also called a SIM port out because of the hacker porting out your mobile number to his/her own SIM card (obviously a private number).
Also Read: Can Your Phone Be Hacked By Your IMEI Number?
The Causes OR Loopholes of SIM Swap
It’s not like there is a hard and fast list of causes that occur in this incident. However, there are a few that give enough time to the hacker to get things done.
For example, if a user’s phone has been stolen or he/she is switching to a different telecom company. In this period, the security vulnerability increases, and this gives a window to the hacker.

The way about getting details isn’t something new, that can be phishing emails, lucrative text messages. All they need to do is call your telecom customer care, impersonate you with your details, and port your number. A minor but there can be a probability of telecom employees being bribed by the hackers to change the SIM number.
So if you talk about the probability hackers have, sky’s the limit for them. We either ignore these or don’t bother about someone getting access to our account without even realizing it.
Also Read: How To Track A Lost or Stolen Android Phone
Can You Prevent Yourself From Becoming A Victim of SIM Swap?
There is a saying – “If there is a problem, there is also a solution. All we need to do is either look around more or dig deeper.”
So yeah, you surely can prevent yourself from becoming a victim of SIM swap scam. It’s actually quite easy to use these methods to keep yourself out of the SIM swap attack zone.
1. Don’t Access Phishing Scams
Emails, links, text messages you name it, they have got access to each and everything to make it look original and safe. However, it’s you who need to make sure that you check the source before even accessing the link given in the notification alert. For starters, just don’t access a new & unknown URL given in the text/email. Don’t keep signing into a website platform you don’t know about and keep yourself away from downloading stuff from unknown resources.
If you fail to do any of them and the hacker gets control of your SIM card, you are screwed big time.
2. Stop Using Personal Data Online Excessively
The more we are online, the more we access new pages and put our details on new websites or apps. Exploring is good but keep it to a level that doesn’t affect you anyway.
3. Be More serious About Account Protection
Everyone would agree with me on this that we aren’t serious about our account security. Be it the bank accounts, registered number not the current one, and many more.
For example, the password of almost all the banking platforms must be changed within 3-6 months, however, this should be on a monthly basis. Follow this religiously so that it becomes a habit, not an act.
4. Start Erasing Online Footprints
Leaving online footprints in the virtual world is one of the major reasons these incidents occur and happen. All of the big giants as well as emerging ones, ask you to remember the login credentials or save the password for the website. In order to keep it convenient for us, we do select the option and next time, we won’t have to remember the password or sometimes even login and password both. Isn’t it a bit scary?
It’s not that these companies are involved in this, but we should not leave our confidential info on any platform. It may be misused and who will be responsible for it, You. Who got affected? You. Who should be blamed? You.
Stop saving your credentials on any platform. Keep privacy before convenience or else you will be in big trouble.
Also Read: Why Is Online Privacy Important?
Conclusion
No matter how much you put security layers, they will find a way to get in your mobile phone. And today, getting into your mobile phone is more dangerous than getting in your house. Because at least you are notified if someone comes into your house. Here, you have no idea. A silent and perfect theft.
So be a bit aware and attentive about anything and everything you receive on your cell phone. Keep yourself away from unknown and not secure websites. Don’t give away logins to unauthorized platforms and make it a habit of erasing online footprints.
Has this article been helpful to you? Do share your thoughts and let us know if you have some other point to add to help a user from becoming a victim of SIM swap.






Leave a Reply