There are tons of different VPN service providers available in the market. But not all of them are suited for everyone. Different service providers employ different VPN protocols. These VPN protocols vary in terms of security and speed they offer. Some of us may use VPN for security purposes, some of us may use them to access global content, and some of us may use them to avoid ISP tracking. All of these uses ask for different VPN protocols.
Let’s quickly move forward and know which VPN suits which purpose the best:
One of the best VPNs available in the market that utilize OpenVPN protocol is Systweak VPN. Systweak VPN offers industry best AES 256-bit encryption standard to safeguard the user information and privacy. Let’s look at some of its features:
Wide Range of Servers: Systweak VPN offers over 4500 servers at locations around the world. Wide range of servers to choose from offer higher speed.
Global Content Access: Systweak VPN has servers in more than 50 different countries that help provide unrestricted access to content from all around the world.
AES 256-Bit Encryption: Systweak VPN offers AES 256-bit encryption which makes it virtually impossible for anyone to break the cypher and decode the user information.
Download Now Systweak VPN
Be it streaming or security, Systweak VPN offers best of all world. Systweak VPN is surely one of the best VPN for PC available in the market.

We hope we were able to help you decide the kind of VPN protocol you want to go with. Do let us know about your favorite VPN, we love hearing from you.
Now, when you have the idea of which VPN Protocol suits your need, let’s dig deeper into functioning of these different protocols.
Also Read: VPN Blocked! How Do I Bypass It?
Functioning of Different VPN Protocols:
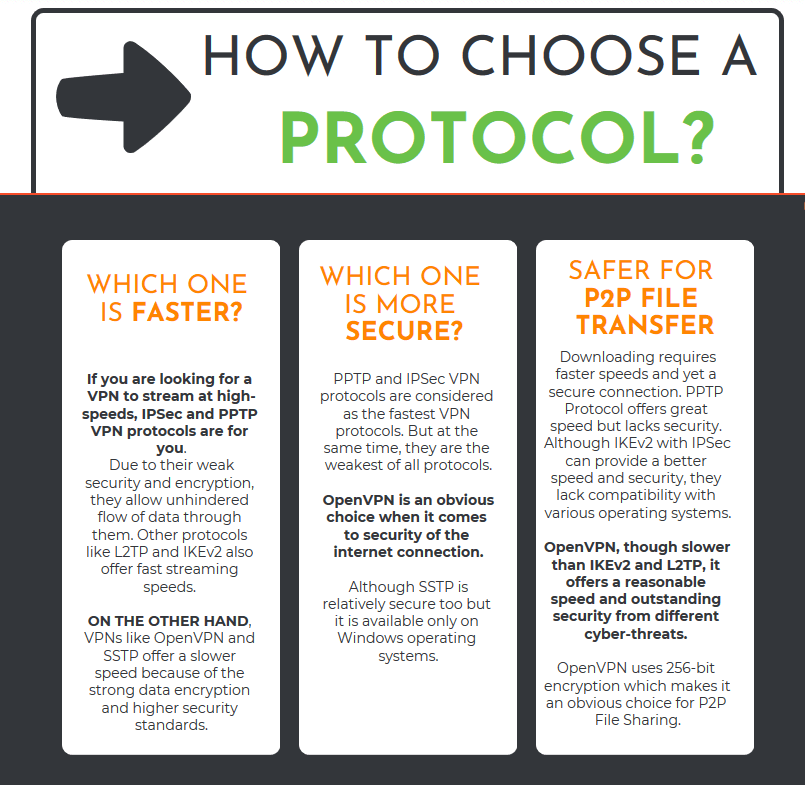
1. PPTP:
Point to Point Tunneling Protocol (PPTP) was created by Microsoft and has been in use since Windows 95. However, PPTP couldn’t offer the security it was intended to. Its security was easily cracked by the hackers and was made useless in just a few months of it releasing.
Because it offers less security when compared with other protocols, it definitely offers the fastest browsing and streaming speed. Not many Service providers use this protocol anymore because of it being unable to serve its purpose.
2. IPSec Protocol
IPSec protocol is widely used in conjunction with other protocols such as L2TP and IKEv2. Although, it can be used separately, it doesn’t provide the require safety that way.
IPSec protocol works on two different modes; Transport Mode and Tunnel Mode. In Tunnel mode, data is sent through multiple tunnels created between the source and destination and is encrypted through different gateways. In tunnel mode, IPSec Protocol doesn’t necessarily require a companion protocol, however, it is suggested to use a companion Protocol.
In Transport mode, IPSec Protocol is requires either the L2TP or IKEv2 protocol to work. In this mode, the data is transferred through a single secure tunnel and data is encrypted in the device itself, not the gateways. The tunnel required to safely transmit the data can be created by either of the tunneling protocols, IKEv2 or L2TP.
3. L2TP Protocol
Layer 2 Tunneling Protocol (L2TP) is used with IPSec protocol. As the name suggests, this protocol is aimed at creating a secure tunnel between the source and the destination. Layer 2 Tunneling Protocol in itself can’t encrypt the data before sending and hence, requires IPSec protocol to do that.
Together IPSec and L2TP offer source to destination security with the help of encryption and secure tunneling.
Also Read: Ways To Monitor VPN Connection On Windows 10
4. IKEv2 Protocol:
Internet Key Exchange version 2 is a widely used VPN tunneling protocol. IKEv2 is also commonly paired with IPSec protocol. As the name suggests it helps provide security from various key tracking malicious websites. It can provide security and speed when paired with IPSec protocol.
5. OpenVPN:
OpenVPN, as the name suggests, is an open source protocol. OpenVPN employs AES 256-bit encryption and 2048-bit RSA to provide excellent security from cyber-threats. Because it provides customizability and an unbreakable encryption, it has gained a lot of popularity in all sorts of Operating Systems. OpenVPN works on two different protocols; TCP and UDP.
Although the speed OpenVPN offers is hampered by deep encryption, it still manages to provide unrestricted and unhampered streaming. Because of all these upsides and compatibility with all the operating systems, it is the most widely used VPN Protocol.
6. SSTP:
SSTP (Secure Socket Tunneling Protocol) is similar to OpenVPN protocol. It too employs AES 256-Bit encryption to safeguard user data from hackers. Similar to OpenVPN, it also utilizes 2048-bit SSL/TLS authentication to authorize only the rightful receiver to decode the data.
Because it is developed by Microsoft, it only supports the Microsoft created operating systems. Hence, it suffers the disadvantage of being unusable with a wide range of Operating systems.
These are the most common types of VPN Protocols used by VPN service providers. All these VPNs serve different purposes and have their Pros and Cons. However, if we have to choose one winner that provides the best of all worlds, it would be OpenVPN. With its wide range of compatibility, second to none security, ability to bypass most firewalls, and capability to provide a fast browsing speed, it surely is the rightful winner.
Next Read
Amazing VPN Advantages Before You Start Using One
How To Set Up VPN On Windows 10?







janny
Which one is the most secure and fastest VPN protocol?