Emails are still the primary mode of communication regardless of social media is boosting up with messenger apps. There are over 4 Billion email users across the world who use Emails on a regular basis. Many of the email users are still unaware that Emails are the major carrier of malware and virus infections.
A virus-infected email attachment can bring down your PC or compromise your valuable information. As people are getting smarter and aware of malicious emails, hackers are also upgrading their skills and preparing new weapons to steal information. With small tips, you can learn how to scan an email attachment for viruses and get real-time protection on every incoming email attachment.
How Malware is Carried With Email Attachments
Whenever you receive an email attachment from an unknown sender, you shouldn’t jump on to open the attachment. Hackers use .exe, .pdf, .xls, .vbs, .doc, and .rtf types of file formats to send malware or viruses. They may also use a known email address that can be a clone of someone in your address book.
How to Spot a Malicious Email Attachment
Suspicious File Extensions
At times, hackers don’t make it easy for you to identify if an email attachment is malicious or clean to open. They use almost the same types of attachments which we use in routine life. But the most vulnerable ones are packed in .ZIP, .RAR, .JAR, .BAT, .VBS, .CMD, .REG, .WSF or .EXE file formats. If you see such email attachments, scan them before opening.
Who’s The Sender
You must have heard of Email spoofing where the sender’s email address is similar to a known email address with a slight change. For example, if a real email address is ‘[email protected]’, the spoof email address can be ‘customer.care’ or ‘[email protected]’, or anything like that. Need not to say that if the email address is tricky, like ‘we4care’ or ‘3456nzy@hotmail’, it is not safe to open such email attachments. If you are receiving an email from your friend in a formal language, you should be suspicious about it when you see your full name instead of a nickname.
“An Email Attachment can be malicious even if the email sender is known to you.”
Catchy File Names
One shouldn’t be greedy to jump on email attachments offering gifts coupons or lucky draws. If you are lucky enough, you will receive a proper notification or calls for the same. Such phishing emails are only meant for fraudulent activities.
You may receive emails with catchy file names like ‘bestopportunity’ ‘luckywinner’ or anything which looks like offerings can be malicious.
Content of the Email
The content of the email can also give you a hint if it is for real or a phishing email. Most phishing emails show urgency and ask you to click on a link or download an attachment. Such kind of spoofed emails or phishing emails are written by Bots containing lousy formatting and a lot of spelling errors.
“Don’t download or install any email attachment to track a package you never ordered.”
Still Suspicious With An Email Attachment?
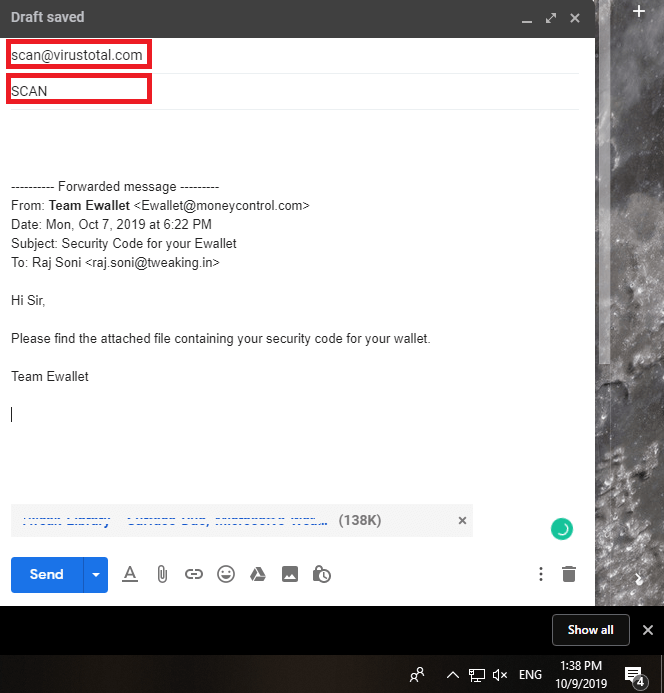
If you are still suspicious of an email attachment, and you don’t know how to scan an email attachment for virus, you can forward the email with attachment for scanning at [email protected].
- Open the Email with Attachment and click on the ‘Forward’ option.
- Enter [email protected] in the ‘To’ field and ‘SCAN’ in the subject line. To edit the subject line, click on the dropdown menu beside the ‘To’ option and choose ‘Edit Subject’.
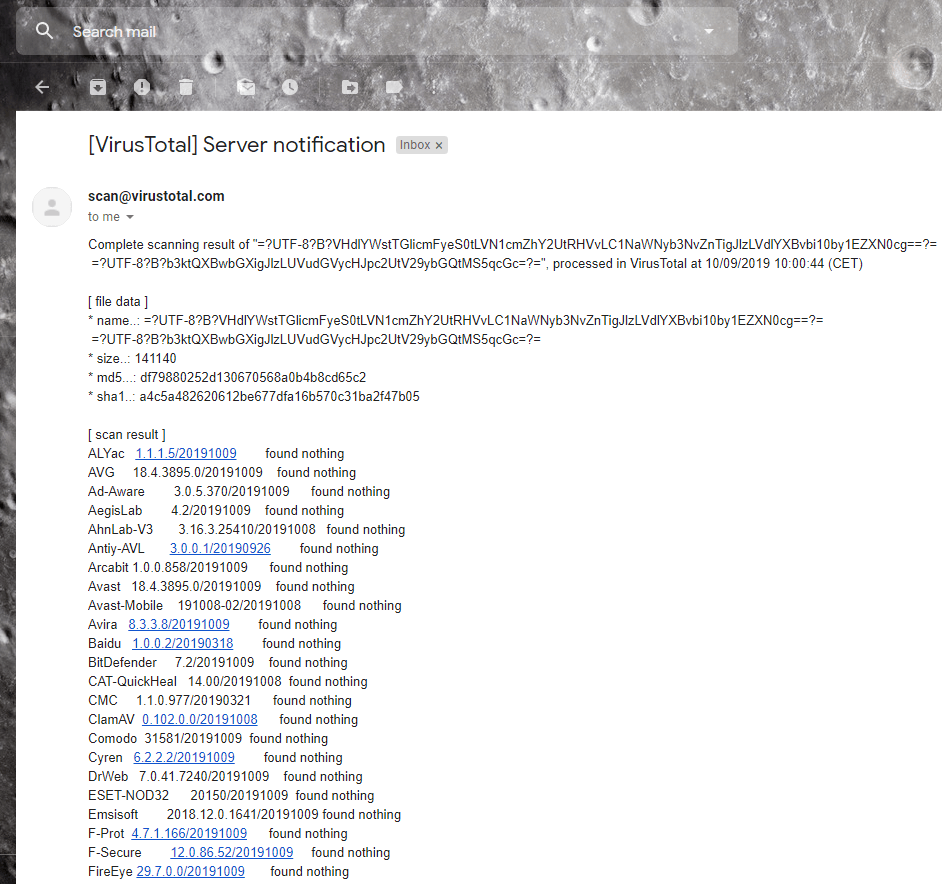
- Once you send the email, you’ll receive a reply from Virustotal which will include the scan result from almost all the antivirus providers. It may take some time to receive the reply depending on the server engagement.
Best Antivirus Protection Software
Norton Security

As per antivirus standards, Norton Security by Symantec is one of the finest products for total security on all your devices. There are various versions of Norton Security based on your requirement from Basic to Premium that gives the same level of security for single or multiple devices including Mobile security.
“Real-Time scan is better to stay protected than recovering from collateral damage.”
Norton is best known for Internet security, malware protection, virus and threat protection and protection against online scams. From VPN to Kid’s safety, it works robustly identifying and quarantining found infections.
Kaspersky Total Security

Next best in the league is Kaspersky Total Security. Kaspersky is one of the best selling security suites to keep all your devices safe and secure 24/7/365. Kaspersky has a range of Internet security, Cloud security, Password Manager, VPN security, QR Scanner, and many inline products bundled within Kaspersky Total Security.
Summing Up
There are hundreds of products in the market however Norton Security and Kaspersky Total Security are the best security software for Internet Security and Total Security of your system. Always ensure that you scan your email attachments before opening them irrespective of a known or unknown sender. Precaution is better than cure, now as you know how to scan an email attachment for virus, stay safe and secured because damage control might not be that effective than keeping it safe.
If this article turned out to be helpful to you, please like and share this with your colleagues. For more such tips, tricks and tech-related updates, click on the bell icon to get regular updates from Tweak Library. Do share your thoughts about this article in the comment section.
Follow Us:






kristen baker
If the malicious or even secure file format could do the same, then yeah, it would be secure. However, to put it another way, I think that a large part of the malice is in the filesystem being sent. If the file is only sent to a sender or sender and not to another server, a sender is still receiving the original email, and the sender has no idea what the file isn't. I do agree that this is a great idea - but it would be nice if you could use a solution based on the file format so that the sender can use a filesystem, or even to send it to a user.
Raj Soni
Dear Kristen, The Tips & Tricks mentioned here in this article are precautionary measures to eliminate the risk factors without using a third-party app. We'll research a few of the apps and add more information to this post. Please stay tuned for more such innovative posts.