Looks like, Intel is going through a rough patch. After Meltdown and Spectre flaw, another secret-spilling security vulnerability is detected in Intel’s chip. Here is how to fix Data Sampling (MDS) vulnerability and how it works?
Meltdown and Spectre flaw that created panic in the tech industry last year were known as side channel attacks. For this Intel had to answer the public and U.S. cybersecurity officials. However, it seems Intel was already aware of other flaws too. But did not mention it as the company was facing rough time due to Meltdown and Spectre flaw.
Although in a statement the company said, users may face similar side-channel flaw in future. This means a new class of speculative execution attacks is not by chance.
The newly exposed flaw is called data sampling attacks and is more dangerous than Meltdown and Spectre. This flaw is discovered by the same researcher who found Meltdown and Spectre flaw, it can leave millions of PC’s exposed to four new attacks i.e. Meltdown UC and Rogue In-flight Data Load (RIDL), ZombieLoad, Store-to-Leak forwarding, and Fallout that Intel calls as “Microarchitectural Data Sampling,” in short MDS. It will allow hackers to read almost all raw data that touches Intel chips.

The latest vulnerabilities and exploits use similar techniques used in Meltdown and Spectre flaw. But, the difference that makes it more severe is instead of leaking values from the cache, it leaks values from various buffers within the processor. Still, Intel rates this security vulnerability as a medium.
Is there a fix for Microarchitectural Data Sampling (MDS) vulnerability?
Since the bug is embedded in the computer hardware architecture, it cannot be fully fixed. However, new Intel chips released this year contain a fix, but this can slow the performance by as much as 19%. Moreover, previous generation chips are yet to be patched.
<blockquote class=”twitter-tweet” data-lang=”en”><p lang=”und” dir=”ltr”> <a href=”https://t.co/pS1MAwBaml”>pic.twitter.com/pS1MAwBaml</a></p>— Daniel Kartafla (@DanielKartafla) <a href=”https://twitter.com/DanielKartafla/status/1128354493320581120?ref_src=twsrc%5Etfw”>May 14, 2019</a></blockquote>
<script async src=”https://platform.twitter.com/widgets.js” charset=”utf-8″></script>
Users using old CPU are advised to update their firmware and software, macOS, Windows, ChromeOS and Linux have already released software updates to address MDS attacks. Intel too has released microcode updates for certain of its hardware (PDF).
But how does Data Sampling (MDS) vulnerability harm you?
To know about it and to understand the process read further.
How does the processor work?
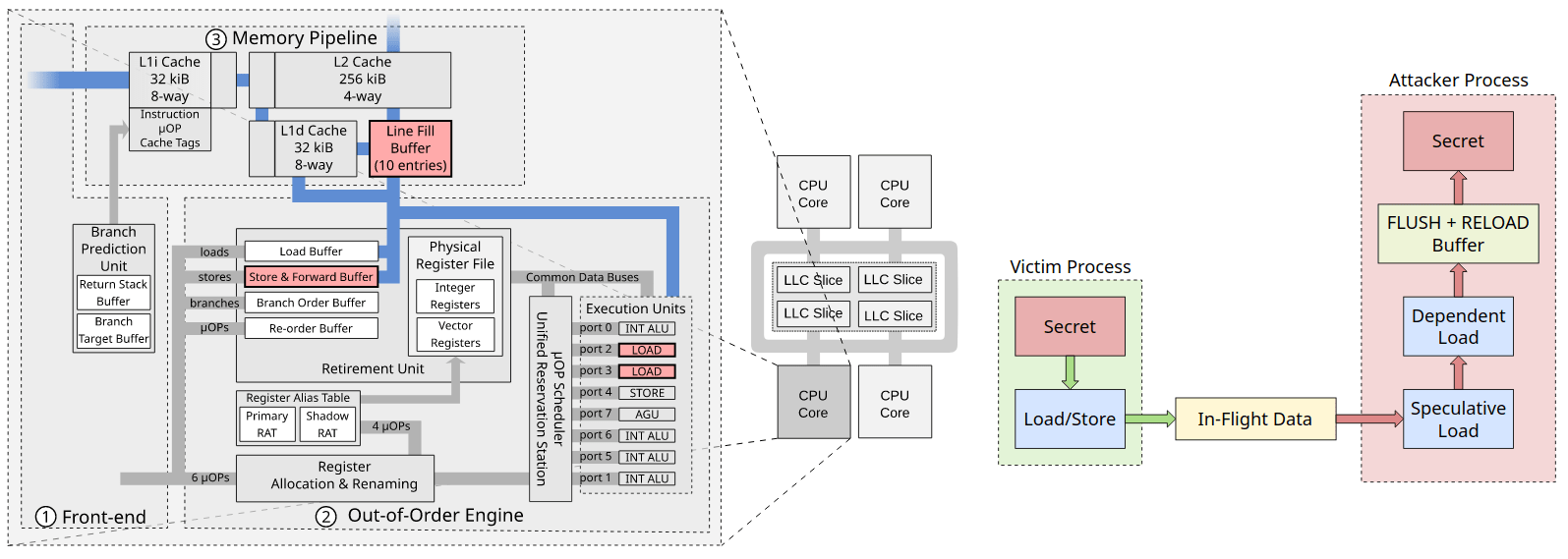
Each processor uses a specialized buffer to move data within.
Line Fill Buffer: holds data from the main memory from a previous fetch waiting for the new fetch to finish.
Store Buffer: can contain mix data from different store operations therefore, a mix of old and new data to load buffer can be forwarded.
Load port: likewise, can contain old data while waiting for the new data from memory.
All these buffers can be used in Microarchitectural Data Sampling attack.
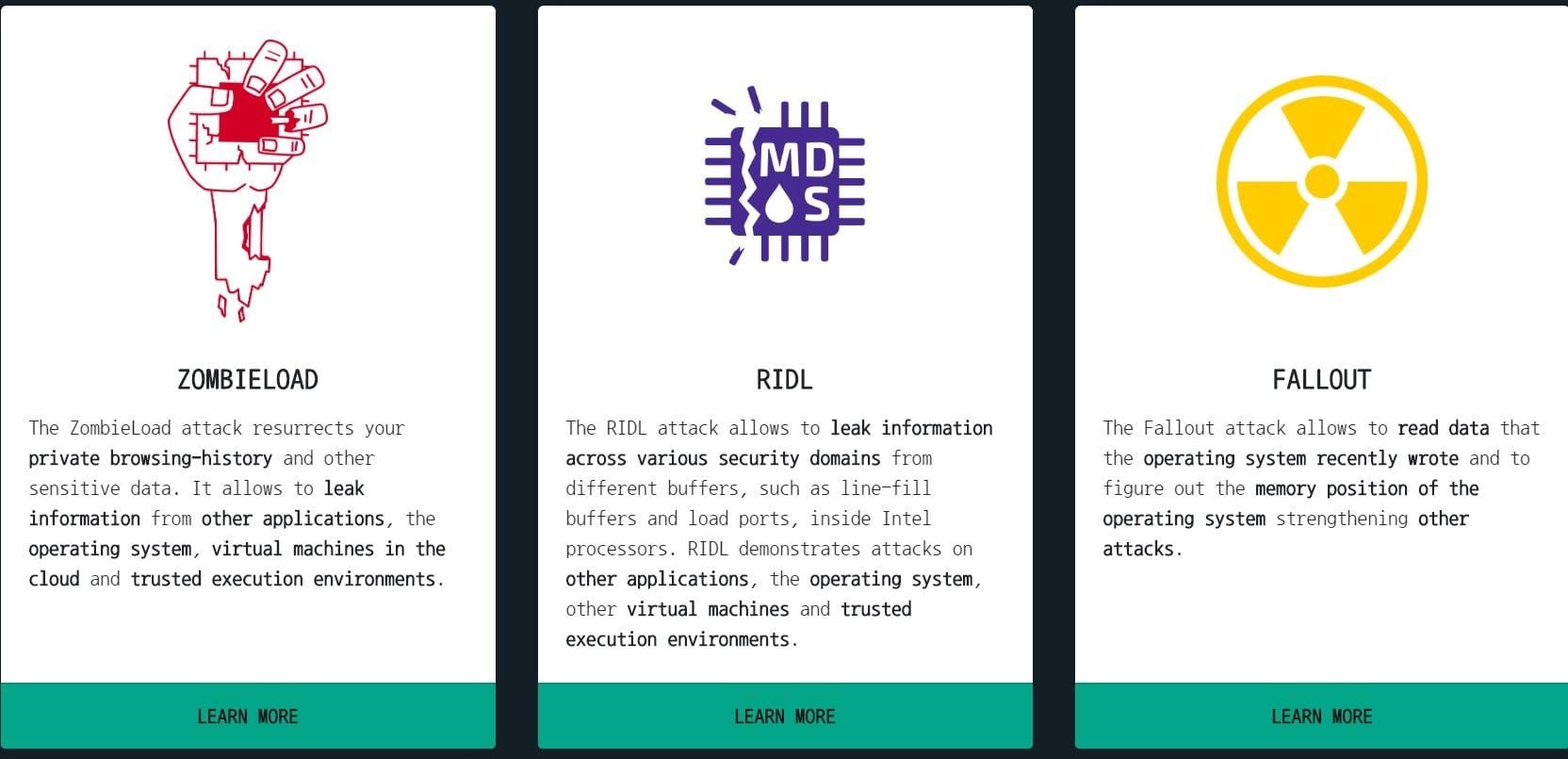
RIDL: exploits allow attackers to leak confidential data across arbitrary security boundaries on a victim system.
Moreover, RIDL exploits three bugs in Intel CPU to leak data from various internal CPU buffers. These buffers are used to load or store data in memory.
Fallout attack: Leaks data from Store Buffers and exploits the fourth vulnerability in Intel CPU. It is used when CPU pipeline is used to store data. This attack will work against Kernel Address Space Layout Randomization (KALSR) protection that works against memory corruption bugs
ZombieLoad vulnerability: Another dangerous exploit that allows threat actors to see locked secrets. This means hackers can see disk encryption keys, browser history, website content, user keys, password and more. Leaving not only the PC’s and servers vulnerable but cloud data also.
Moreover, it exploits Fill Buffers vulnerability leveraged by RIDL that works on both personal PC and cloud infrastructures. This flaw is most likely exploited in situations where PC’s run multiple tasks at a time because data leaked by one application can be read by another.
Due to this cloud infrastructures are at risk because applications from different users run on the same machine, taking advantage of virtualization machine. Therefore, vendors like Microsoft, Amazon, Apple, and Google have started to roll out security warnings instructing users to patch the flaw.
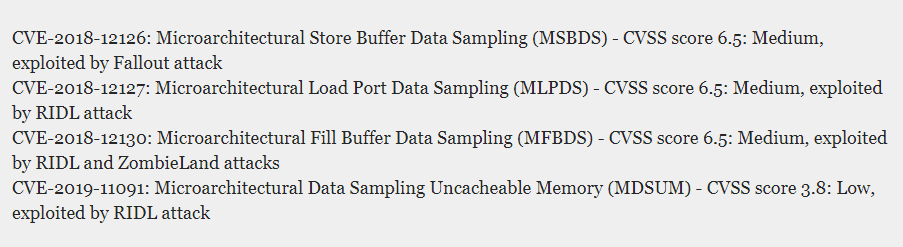
Identifiers for MDS vulnerabilities exploited by RIDL and Fallout
What is the issue?
The latest discovered bug impacts Intel chips made since 2011 and exploits a feature known as “speculative execution” allowing hackers to steal confidential information directly from device’s CPU.
What is Speculative execution?
Speculative execution is a process used to optimize CPU performance by running a task in advance without being called out. This technique is used to speed up modern computer chips, but it also opens the door for attack if the data is pushed in another part of the hardware that attackers can access.
What does this mean for users and for gaming PC?
It doesn’t mean much for gaming PCs and desktops but users should avoid downloading and running random executables.
The threat is greater for cloud services as there’s a potential to steal data from other virtual hosts running on the same system.
Vulnerable Intel chips as reported by the company are:
- Xeon
- Broadwell
- Sandy Bridge
- Haswell chips
- Kaby Lake
- Skylake
- Coffee Lake
- Whiskey Lake
- Cascade Lake
- Atom
- Knight processors
For more information refer to mdsattacks.com
This might sound like another security loophole that needs to be patched. But it also shows that there are more Intel processors out there that need to be patched. Although researchers who found out the law says it is hard to exploit but nothing is impossible. If before the patch is released attackers can exploit it then, no data is secure. Neither on the personal computer nor on the cloud.





Leave a Reply