Whenever we receive an email, our eyes directly go to the sender. We check the sender details and then we check the content. While working on official email IDs, sometimes we need more information regarding the sender. So, from the basic information from the sender (Email header), we can use it to trace an email back to the source. Through this blog, I am going to highlight how to trace an email back to the source.
Why do we need to trace an Email Address?
First of all, we need to understand why we need to trace an email address. Nowadays, we receive malicious content emails frequently. Spam, malware, phishing emails, and scams are so common in our inbox. If you will see more properly and will research a bit, you can see the sender’s information easily.
After this, you can easily block such spam and scam contents from your inbox permanently. Server administrators remove such emails from our inbox permanently.
Also Read: Know If An Email Attachment is Malicious Or Safe To Open
How to Trace an Email Address
You can easily trace an email address only by looking at the email header as the header of the email contains email metadata and routing information. However, routing information and metadata are the things we never cared about while receiving a spam email. But, such information is important to trace the source of the sender’s email.
The fact is that most of the emails do not display the full header of the emails as per standard visuals as they are full of data that seems useless to an untrained user of the email. But, some of the clients offer ways wherein you can check the full email header. All you need to know is where to look when you are looking at an email with technical data or spam.
Below mentioned are the steps on how to trace email back to the source IP address.
Email Header
Open your email account, and then open the email you wish to trace. Click on the drop-down menu available in the right-top corners, and click to Show original from the menu option.
Outlook: Email header
After this click on the email, you wish to trace, click on the head to File>Properties. The information will appear in the “Internet headers”.
Apple: Email Header
In your apple email, open the email you wish to trace and head towards View>Message>Raw Source.
We know that there are various email clients. But, an internet search will reveal “how to find a full email header” in your email box. Once you have gathered on all information in a full email open header, you will see the data in more of a technical form. But, do not panic, in the next section, I am going to tell you how to understand the data in Full Email Header.
Understanding the technical data in Email Header
Once you take a look at the technical information, you will see a lot of information. However, let me make it easy for you.
Read the email header in a chronological manner, like from the bottom to the top (old information present at the bottom), and you will see that each new server is added in the data from which the email traveled.
You can see the sample of my Gmail account email header:
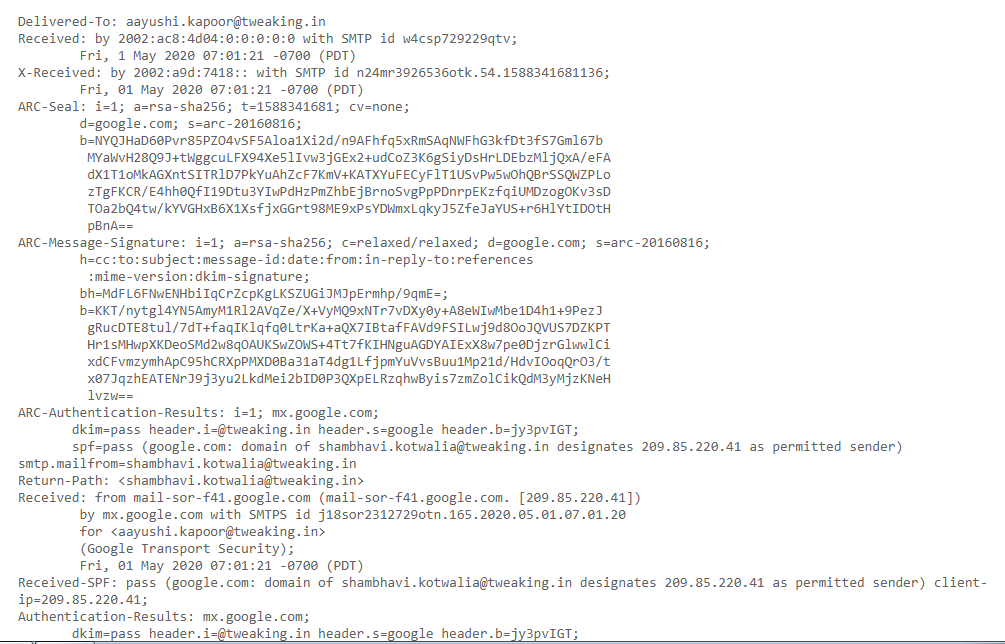
Understanding the Gmail Email Terms and Lines
Maybe when you see unfamiliar terms, you can get confused; therefore, take a look to understand your email account:
From
From displays the information of message sender
Content-type
The Content-type tells your email client or browser how to interpret the information.
MIME-Version
Mime-Version shows the email format in a standard way.
DKIM-Signature
“Domain Keys Identified Mail” shows the domain the email should be protected from sender fraud and email spoofing.
Authentication-Results
Authentication results have a full record of the checkout carried out.
Received-SPF
Sender Policy Framework (SPF) constitutes the part of the authentication progress which generally stops the sender from forgery of the address.
Return-path
It refers to the window where all the bounced and non-send emails end up.
ARC-Authentication-results
The Authenticated Received Chain is the authentication standard that identifies all the email servers and intermediaries which forwards your messages to the receiver.
ARC-Message-Signature
The signature of the email takes a screenshot of the message header for further validation.
ARC- Seal
The ARC results and the signature verify the email content as similar to DKIM.
X-Received
X-Received differs from the received and considered as non-standard, as it might not be the permanent email of the sender.
X-Google-SMTP Source
X-Google-SMTP-Source shows the email transfer with the use of Gmail SMTP.
By understanding all these terms, you can trace the original sender of any email containing malicious content.
Tools to Trace IP Addresses and Emails
With these famous tools, you can trace an email back to the source IP Address.
I hope the blog was helpful. For more content, follow Tweak Library on all social media platforms.
Thanks for reading.
Read Also:
A Guide To Protect Yourself From Spear Phishing Attacks
Cyber Threat: Latest Computer Virus


Leave a Reply