The political tensions between North Korea (formally known as the Democratic People’s Republic of Korea) and the United States are at an all-time high since North Korean leader Kim Jong-un has revealed his plans to make nuclear weapons, seemingly to wipe out his “enemies”. Lately, North Korea, knowing that it can’t just outmatch the United States at military strength and economy, has turned to network hijacking and cyberattacks to make the US vulnerable and is regularly trying to breach into government files and information. The attackers, which claim to be private organizations and having no connection to the North Korean government, have made several attempts on US private organizations and government institutions. They’ve even gone to lengths of giving open threats of terrorist attacks and massacres if US officials do not give in to their demands. Once again, North Korea’s apparent state-funded cyber attacks have targeted US government agencies with a new malware dubbed HOPLIGHT. What HOPLIGHT can do and what’s North Korea is after this time?
Must Read: Building Blocks Of Cyber Security
North Korean Cyberattack Attempts at the US

HOPLIGHT is not the first time North Korean cyber attackers have targeted a United States entity or firm. In fact, this has been going for almost half a decade now; and while North Korean regime continues to deny to have any information on these attacks, it is a world known fact that the regime has been regularly backing them up.

The first major attack, which made headlines was the Sony Pictures Hack, wherein the attackers hacked into the servers and networks of Sony Pictures, an American film studio. The attack targeted personal emails of studio heads, data files, scripts of upcoming film releases, and details of some contractual agreements under process. The demands were to block the release of their film The Interview, which was a mockery to North Korean leader Kim Jong-un. The treats of terrorist attacks at the film screening forced the studio to give in the demands. The United States government then began a series of investigations.
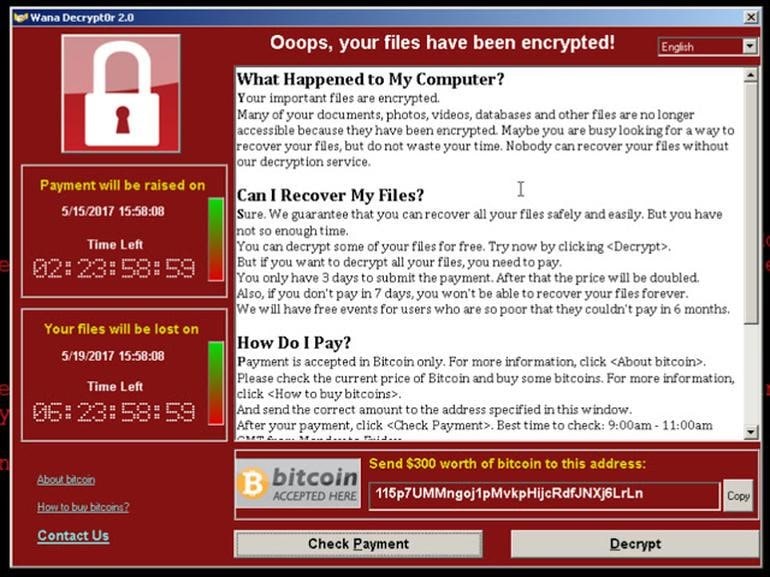
In 2017, a hacker group called The Shadow Brokers used a Microsoft Windows vulnerability to carry out worldwide cyber attacks, hijacking corporate servers, and accounts. This Denial of Service attack called Ransomware violated over 200,000 computers worldwide, and attackers demanded ransoms in cryptocurrency to revoke their blockade over these computers. It was then that the US government raised stakes over their ongoing investigations and started digging internationally. By the time, US officials traced the attacks to North Korea and confirmed official charges, it had already suffered more highjacking attacks on its utility services and electricity grids.
So, Who Were Behind These Attacks

The United States government, Federal Bureau of Investigation (FBI), and US Department of Homeland Security (DHS) that these attacks were backed by the Korean intelligence group Reconnaissance General Bureau, and were orchestrated by Bureau 121, codenamed the Lazarus Group and called by many more names. Bureau 121 is said to be an expert team of cybersecurity experts and trained hackers, which are solely responsible to carry out such breach operations on “enemy” nations of North Korea. The investigations specifically named Park Jin-hyok, an alleged member of Bureau 121, who has been the lead handler of these attacks. And meanwhile, the North Korean regime has declined existence of any such group and has refrained from an official statement on these attacks.
HOPLIGHT: The Latest in Line of North Korean Malware Attacks

North Korean cyber attack group have now released a new malware called HOPLIGHT, which is once again targeting US government agencies for information and data. Though no official account of any HOPLIGHT attack on a private or public organization hasn’t been out yet, the malware has been detected and traced back to North Korea by US Computer Emergency Readiness Team (CERT). FBI and DHS have released information that this new malware acts as a trojan and can read, alter, and move important files in the system. The malware also has the ability to inject virus codes into running network processes and terminate or halt them, that can create disruptions in agency work. Moreover, the malware is able to alter registry files, which can hamper data stored in public agency networks.

CERT has released details of nine different type of files, most of which are proxy applications, that are being used to inject HOPLIGHT into systems and networks. The proxies carry fake SSL certificates and use command servers to carry out breach operations.
HOPLIGHT is the New Thing In Town
Since Wannacry Ransomware attacks, CERT has been actively publishing reports in regard to malicious cyber attacks and possible malware detections in order to warn the agencies and public organizations. And none of these reports has previously addressed anything like HOPLIGHT and hasn’t included any addresses with HOPLIGHT. Apparently, HOPLIGHT has never been used before and is the newest malware in the list of Bureau 121’s malicious software.
Why North Korea Continues Its Cyber Attacks on US Agencies?

North Korea is a small dictatorship regime, far out in the east and is not capable of taking supreme nations like America. Not on military fronts at least. The nation is surrounded at sea by US naval forces and has been constantly downgraded by world media due to the malicious intentions of North Korean leader Kim Jong-un against world peace and security. Moreover, the country’s weak education and economic system have rendered nation penniless and therefore, the motives behind these attacks have also been financial gains. And of course, no nation can out front carry out espionage, whereas a cyber attacker is undetectable or nevertheless, is impossible to apprehend outside law enforcement’s reach. So, cyber attacks and cybersecurity breaches remain as the most feasible option for North Korea to actively involve in information procurement and intelligence, a practice followed by every other nation in espionage.
But, How North Korea is Able to Carry Out These Breaches?
It is a very viable question, giving the fact that North Korea has been able to execute highly impacting attacks, despite restraining from an online presence on a large scale. The nation has two internet connections with the outside world, and still, it has managed to become a deadly and quite powerful cyber attacker.

This is because the regime has been training youngsters extensively in cybersecurity and hacking extensively. According to DHS and FBI investigations reports, the young lads of North Korea are evaluated on their mathematical and logarithmic skills and are trained to become experts in hacking under state-funded projects. A many of these trained hackers reside in foreign lands, living undercover to provide on-ground intelligence to North Korea.
How big is the problem?

North Korean latest HOPLIGHT interference have though been detected, its threats cannot be overlooked this early. North Korea hasn’t been quiet since last two years over cybersecurity attacks and has even its involvement in any of these attacks under the disguise of fake talks and quietness over the potential nuclear weapons development. In fact, the attacks were continued even after an official meet between US President Trump and Kim Jong-un. So, the problem is quite big and it doesn’t seem to go away soon.
North Korea has already tried direct smash-and-grab attacks before, but HOPLIGHT is a new form of espionage for North Korea, which, yet has not officially targeted any organization.
Must Read: Is Government and Military Data Safe From Cyber Attacks?
The answer to whether North Korea will further its movements with HOPLIGHT or it would retreat in the light of early disclosure of its new malware cannot be fixated yet. However, with never-stopping breaches and hacking attempts from nation’s state-backed groups means that North Korea’s hacking expertise needs to be dealt with.






Leave a Reply