Recently, in a combined report released by RiskIQ and Flashpoint light has shed new light on activities performed by several online criminal groups. These group use JavaScript to skim card details and are named as Magecart by researchers at RiskIQ. They have been active since past three years.
For some, this may be confusing as Magecart, in the past was used to describe a malware installed by hacking group in its first attack detected in 2016. And now, Magecart the name is used to define activities of seven hacking groups.
Key Pointer: These digital card skimmers work like physical card skimmers and the type of attacks performed by them is known as “cross-site scripting.”
What is Magecart?
With this question like, who is/who are Magecart? Is it an umbrella term for anyone using such method? What can be done to stay protected from these widespread attacks? Rise.
In a 59-page report submitted by these companies Magecart is defined as an umbrella term, under which, as of now seven different cybercrime groups are recognized. All of them have their own tactics, targets, skimmer, and other elements.
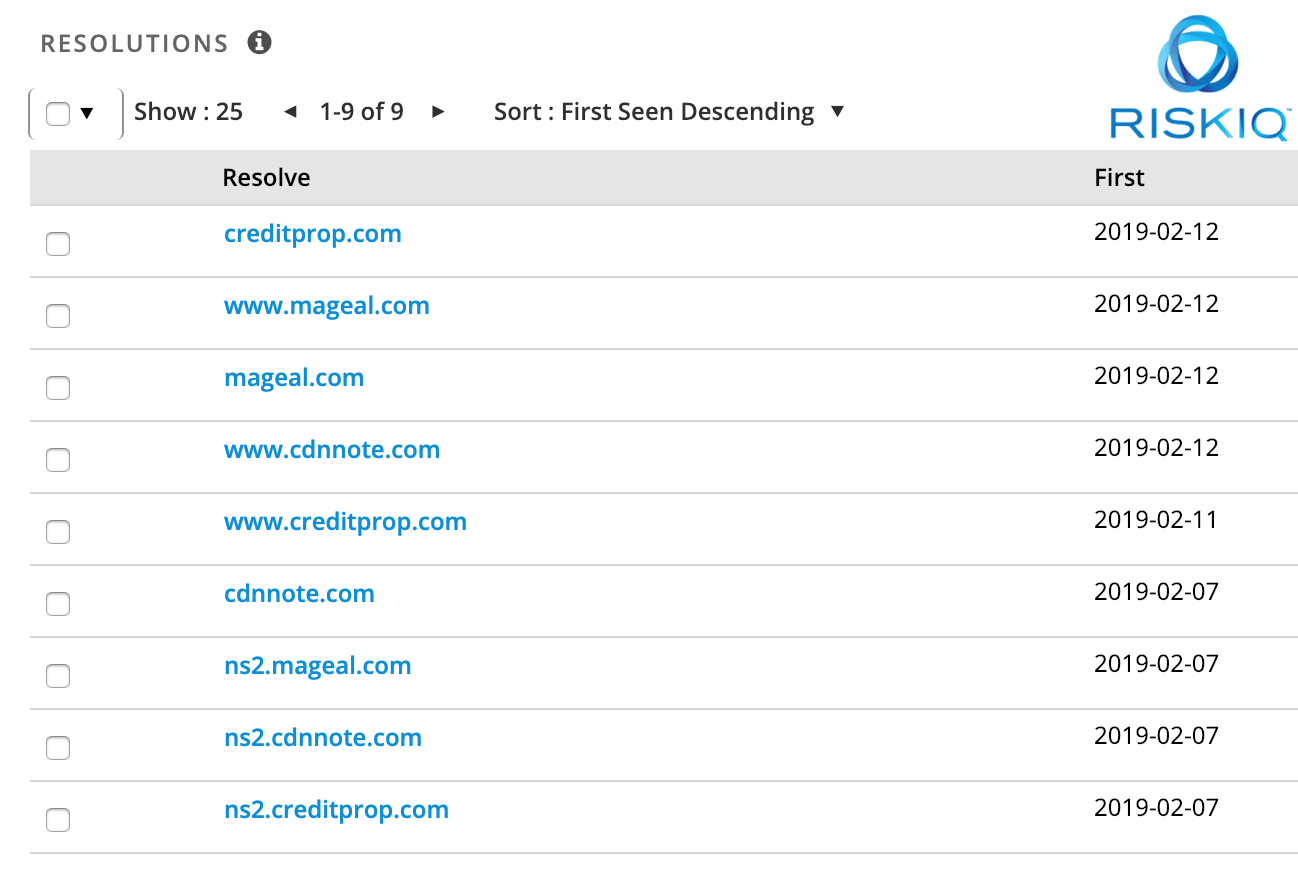
Five adversaries used by Magecart
These groups remained unnoticed for about three years, until recently after targeting British Airways, Ticketmaster and other high-profile destinations, they gained attention.
An insight to Magecart’s Groups
Group 1: identified in 2015 has targeted 2,500 victims till now. This group uses computerized tools to compromise site and upload skimmer code.
Group 2: In late 2016 group 1 started to act as a Magecart Group 2, hence it is combined into one. This group uses automated tools.
Group 3: since 2016 researchers have kept an eye on this group.
Group 3 aims to collect as much detail as possible to hit a large number of victims. Till date more than 800 victims have been compromised. This group takes a different approach instead of checking the URL, the group checks if any form at the checkout page contains card data. This makes it unique when compared with other Magecart groups.
Group 4: advanced group, tries to mix up with regular web traffic to hide in plain sight and register domains by copying analytics providers, ad providers and others.
Group 5: this group primarily targets third party service providers. For the first time it was seen in 2016 and has 12+ victims.
Group 6: This group uses simple skimmer technique and targets top tier companies like British Airways and others.
Group 7: Last group in this list does not have a defined modus operandi. This group attempts to compromise any detected e-commerce group. Plus, compromised sites are leveraged as proxies for its stolen data.
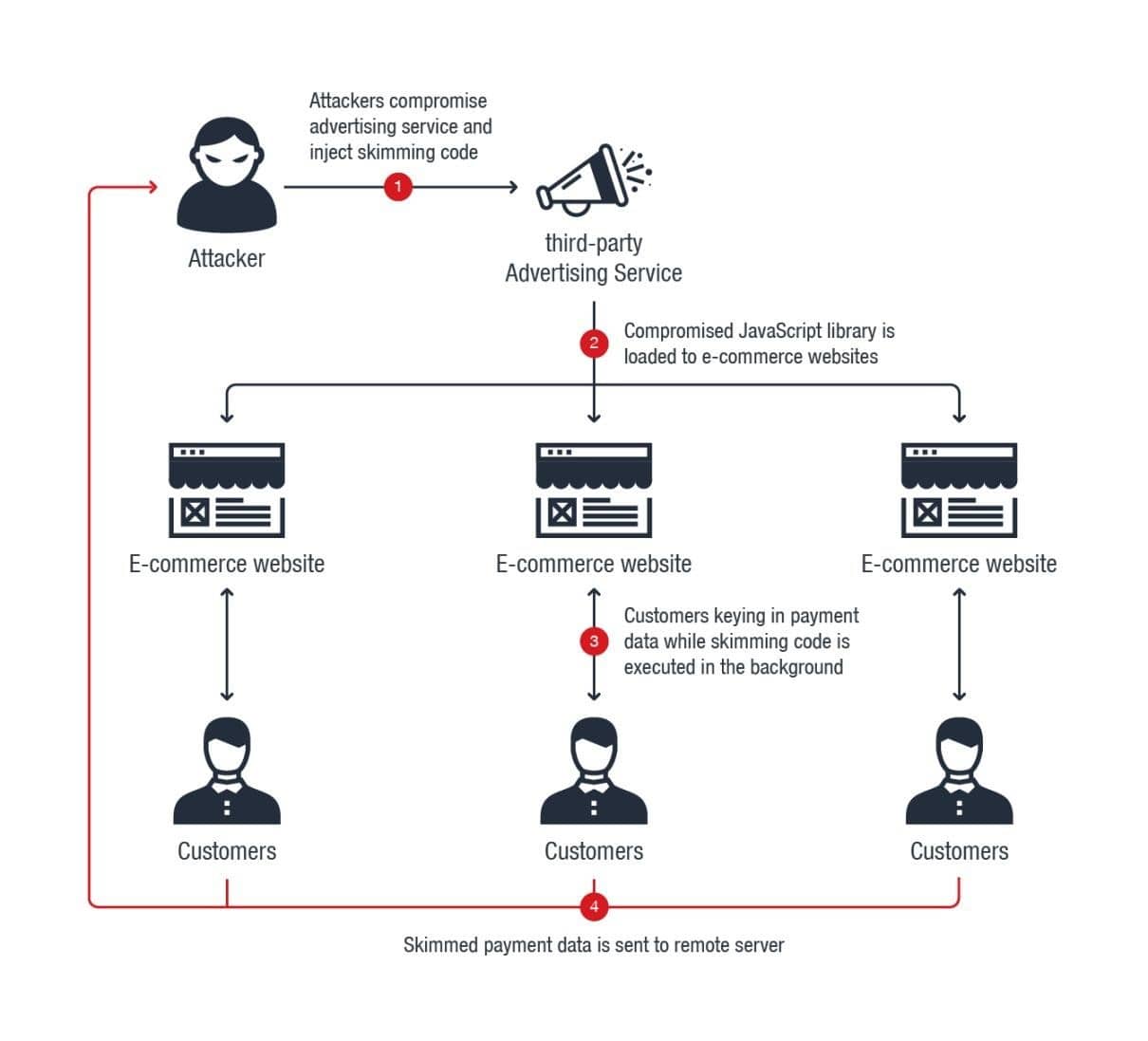
Image Source: blog.trendmicro
How Magecart attack takes place?
All hacks performed by Magecart group are well-established and they follow a pattern. The first step used by hackers to gain access of online store’s backend is to search for vulnerabilities and access infected system.
This same approach was used by Magecart to target Magento stores. To perform this attack hackers used automated scanners to search for Magento stores online and used vulnerabilities in the Magento CMS to gain hold of infected systems.
Once the information was collected hackers changed site’s source code, to load a piece JavaScript that would keep an eye on the payment forms at the checkout pages to access new data entered by users.
Timeline of web skimming activities
Companies attacked by Magecart
- Magento
- PertaShop
- OpenCart
- Custom-coded platforms
In addition to this, it is also observed that some groups do not go directly after the shop. Instead they target third party services on the site like chat widget, support, rating widget and others.
How hackers use these third-party services?
Threat actors find a middle ground and hide their malicious JavScript code into these widgets to skim. This is how recently most big Magecart hacks took place.
Recent compromises are:
- Ticketmaster
- ABS-CBN
- Feedify
How stolen card details are converted into money?
Stolen details are of no use if they cannot be monetized. Therefore, the easiest way adopted by Magecart group to convert card details into money is to put up a sale on card forums i.e. dark web forums.
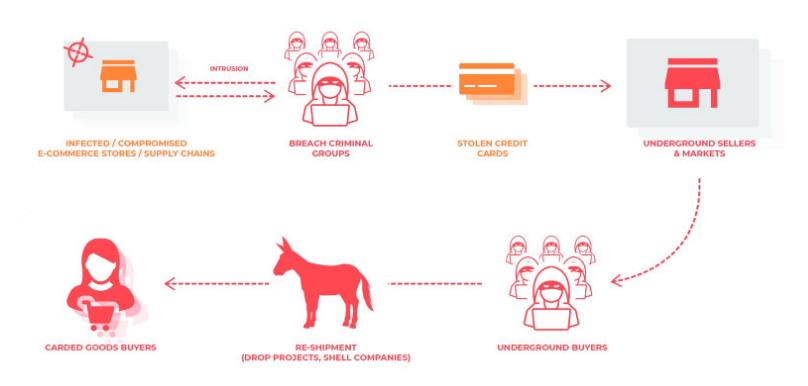
Usually cybercriminals and other groups specializing in money laundering are interested in buying such details. What they do is they buy expensive products using the card details known as money mules and sell them to other location at a cheap price converting the price from compromised card into laundered money which is distributed amongst mule group members.
What is the number of Magecart groups?
Currently, seven Magecrat groups have been tracked by RiskIQ. According to a rough estimation, these groups are responsible for hacks on more than 110,000 different shops.
How were these hacks performed?
- These group fool individuals and job seekers into shipping items purchased via stolen cards
- Mass target online sites, but stay away from high-end shops
- Each group has different skimmer and server infrastructure
- Checkout pages are identified by skimmer by looking at page’s source code for checkout
- These groups use automated tools to identify compromised sites
- According to RiskIQ some of these groups might have developed banking trojans even before getting into online store hacking
- Skimmer code is too big, and it works by displaying a fake form over genuine checkout form. Plus, it contains anti analysis actions to prevent security researchers from examining it
- The aim of this group is to collect as much data as possible and they usually are behind third-party service providers
- Skimmer codes are usually activated on basis of URL keywords
- Group goes only after high profile targets
How to stay protected?
- Disable JavaScript inside the browser before making a payment. This practice will prevent card skimming code to run thus preventing Magecart attack.
- Be watchful, keep a check on your bank and credit card statements/accounts for suspicious activity.
- This type of attacks will continue to take place; hence we need to act smart. Tools like Advanced Identity Protector, will help to secure your card details from ID theft. Plus, it will add an extra layer of protection to help shield your identity.
By keeping these small things in mind, we can stay protected from skimming and other types of digital attacks. If you are thinking this will affect your online shopping experience? Then stop thinking, because most modern e-commerce platforms are designed to work even when JavaScript is disabled.
Must Read: How To Disable Your Credit Card Information From Chrome
Your data security is of utmost importance, therefore focus on it.
We hope you found the information shared interesting and useful. If so, please share it with others and do leave us a comment. Your feedback helps us to know what you like and what would you want us to write.






Leave a Reply